Bitdefender Threat Debrief | July 2024

Staying ahead of ransomware attackers, let alone any threat actor, is a constant battle for security teams. By monitoring trends in victim data, attack methods, and targeted industries, we can gain valuable insights into the evolving tactics of these cybercriminals. In this edition of the Bitdefender Threrat Debrief, we analyzed data from ransomware group websites from June 1 to June 30, identifying a total of 339 claimed victims.
Now, let’s explore the most notable ransomware news and findings since our last :
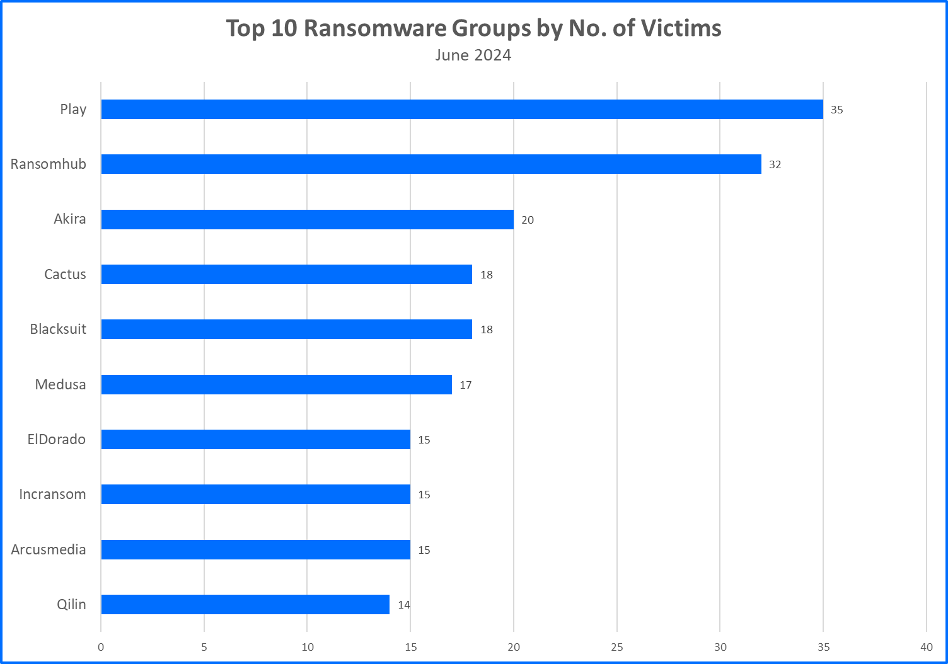
- LockBit Drops Out of the Top 10: Various news sources reported an increase in the volume of LockBit 3.0 ransomware attacks after spring of 2024. As of July 2024, LockBit has fallen from Bitdefender’s Top 10 Ransomware Families. That decline was likely a result of the increase in law enforcement operations and other initiatives to disrupt ransomware attacks such as Operation Endgame, the largest coordinated, international operation against botnets and the dropper malware ecosystem. This resulted in the takedown of more than 100 servers, the seizure of more than 2,000 domains, and four arrests.
Another variable that may come into play is the reporting of illegitimate LockBit attacks (victims reported did not align with findings). The evolution of competing ransomware groups is another variable to consider; new competition among threat groups can shift the number of targets available for established groups and compound the resources needed to launch an effective cyberattack.
- New Eldorado Ransomware Targets Windows, VMware ESXi VMs: A new ransomware as-a-service (RaaS) called Eldorado emerged in March and comes with locker variants for VMware ESXi and Windows. The gang has already claimed 16 victims, most of them in the U.S., in real estate, educational, healthcare, and manufacturing sectors. Eldorado is an emerging threat group that, like the previously reported CACTUS now in fourth place, quickly advanced their position to make the Top 10 Ransomware Families.
- New Ransomware Scam Calls Until You Pay: A new ransomware group has been discovered harassing its victims on the phone until they pay up. A report from anti-ransomware company, Halycon said that Volcano Demon was seen going after “several” targets in the last couple of weeks, deploying a new encryptor called LukaLocker.
Top 10 Ransomware Families
Bitdefender’s Threat Debrief analyzes data from ransomware leak sites, where attacker groups publicize their claimed number of compromised companies. This approach provides valuable insights into the overall activity of the RaaS market. However, there’s a trade-off: while it reflects attackers’ self-proclaimed success, the information comes directly from criminals and might be unreliable. Additionally, this method only captures the number of claimed victims, not the actual financial impact of these attacks.
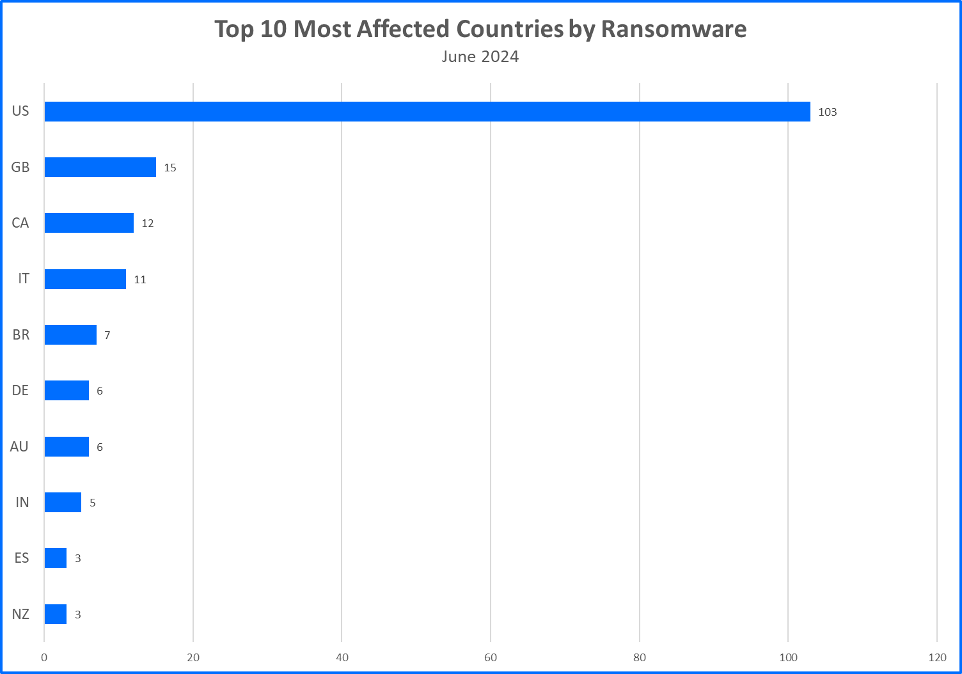
Top 10 Countries
Ransomware gangs prioritize targets where they can potentially squeeze the most money out of their victims. This often means focusing on developed countries. Now, let’s see the top 10 countries that took the biggest hit from these attacks.
About Bitdefender Threat Debrief
The Bitdefender Threat Debrief (BDTD) is a monthly series analyzing threat news, trends, and research from the previous month. Don’t miss the next BDTD release, subscribe to the Business Insights blog, and follow us on Twitter. You can find all previous debriefs here.
Bitdefender provides cybersecurity solutions and advanced threat protection to hundreds of millions of endpoints worldwide. More than 180 technology brands have licensed and added Bitdefender technology to their product or service offerings. This vast OEM ecosystem complements telemetry data already collected from our business and consumer solutions. To give you some idea of the scale, Bitdefender Labs discover 400+ new threats each minute and validate 30 billion threat queries daily. This gives us one of the industry’s most extensive real-time views of the evolving threat landscape.
We would like to thank bitdefenders Vlad Craciun, Mihai Leonte, Andrei Mogage, and Rares Radu (sorted alphabetically) for their help with putting this report together.
