Log4Shell – The call is coming from inside the house

On December 9, 2021, Apache disclosed CVE-2021-44228, a remote code execution vulnerability in Log4j logging library – assigned with a severity of 10 (the highest possible risk score).
We previously documented there is no known risk to customers from our products and services and published a technical advisory with overview and specific examples of attacks from out telemetry. In this blog post, we discuss attempted attacks to exploit the Log4j vulnerability and the countries where these attacks are originating from and where victims are located.
We are presenting the following data from our honeypot network, but also data from our telemetry from hundreds of millions of endpoints. When we started analyzing this data, we were surprised to see a very different picture than we were expecting, with western countries listed as the top source of attacks including Germany, United States and Netherlands.
Our first thought was that these countries are known for hosting infrastructure-as-a-service data centers, and many of these attacks are probably coming from ephemeral virtual machines. We started looking at AWS/Azure/GCP regions and source addresses, but only a small percentage of these attacks originated from these cloud providers.
Then, our researchers continued with more thorough investigation, and we identified a significant number of source IPs as exit nodes for Tor (The Onion Router). After analyzing all unique source IP addresses, over 50% have been identified as Tor exit nodes. This means attackers are using a network of virtual tunnels to stay anonymous and prevent disclosing their origin location.
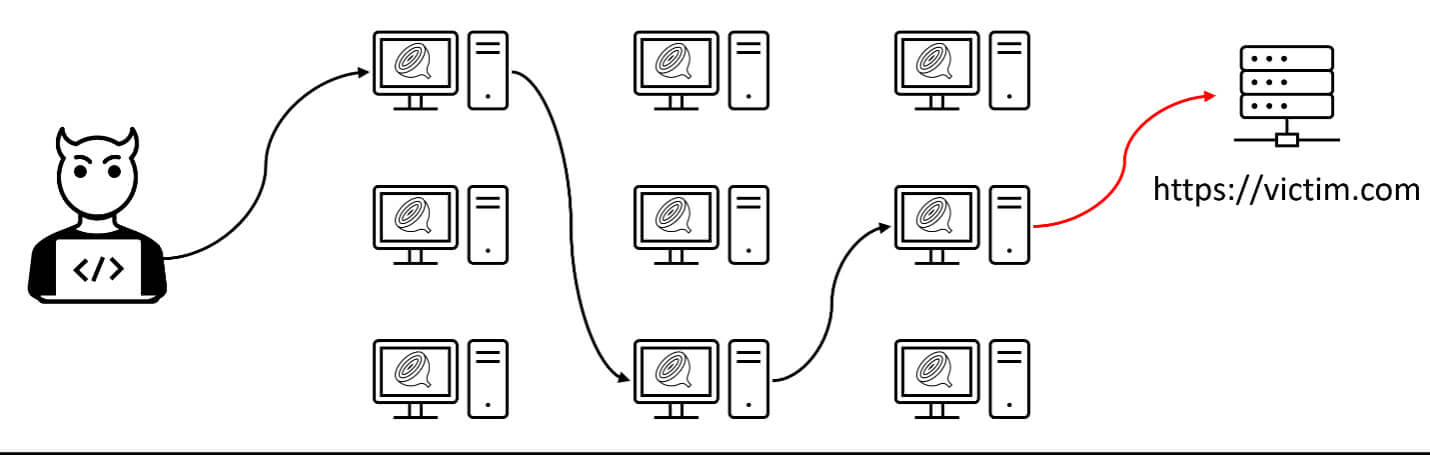
The Tor network allows threat actors to re-route their attacks
In other words, threat actors exploiting Log4j are routing their attacks through machines that are closer to their intended targets and just because we don’t see countries commonly associated with cybersecurity threats at the top of the list does not mean that attacks did not originate there.
Honeypot detections
Starting with honeypot detections, we have seen 36,000 attacks against our network from December 9th through December 16th. Our honeypot network mimics likely targets and collects data about attempted attacks. After an exploitation attempt is made, we block the attack and revert the honeypot to its original state. (We don’t let threat actors finish their attack, so our machines don’t start attacking other networks.) IP addresses of our honeypot servers are not advertised anywhere, so to reach them, threat actors are first scanning the whole IPv4 range.
This graph represents the countries where observed attacks are originating from, not countries that are being targeted. These 10 countries combined cover 87% of our detections.
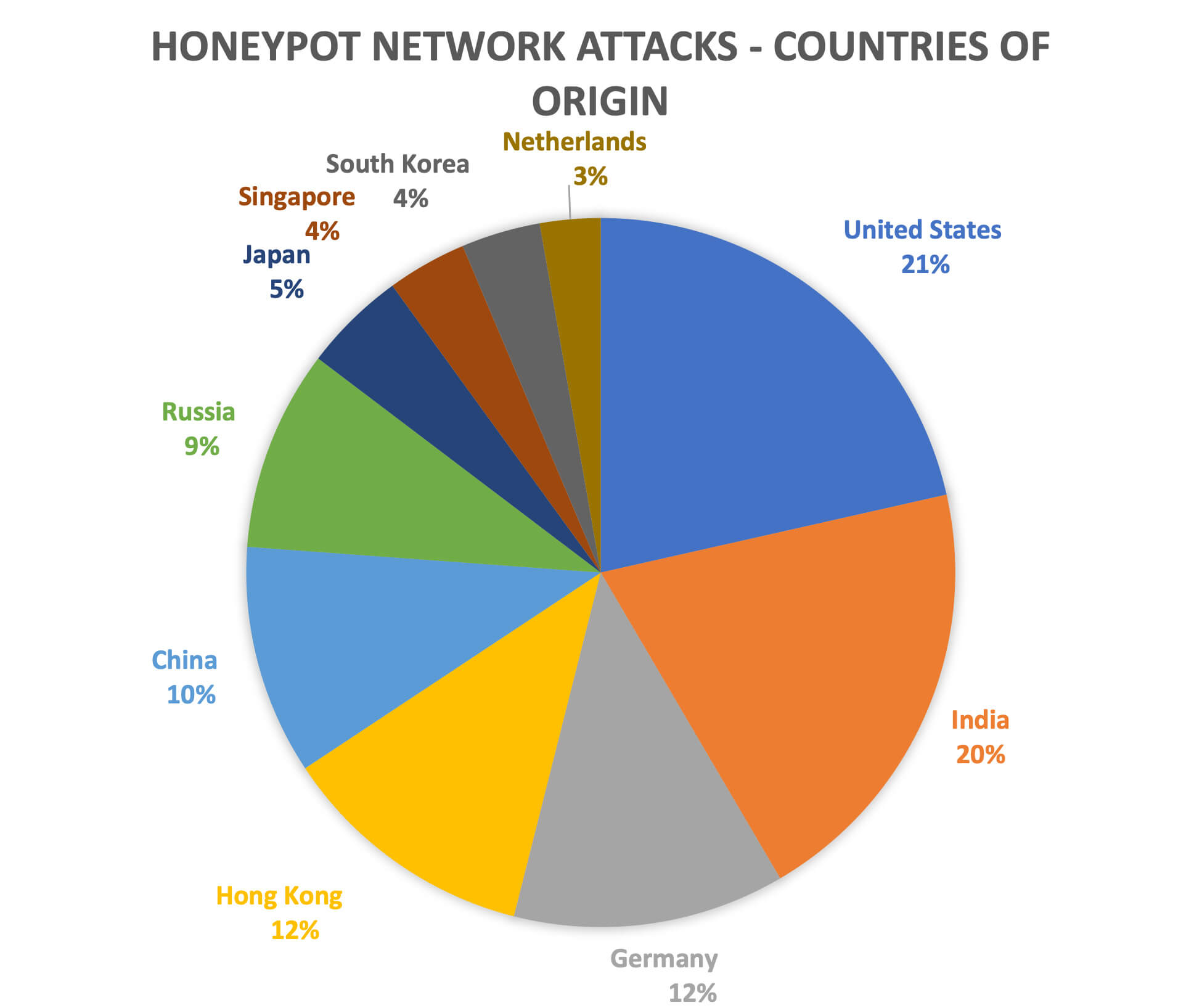
Countries where Log4j attacks on honeypots originated
Surprisingly, we see countries that are usually located in the “Target” column, not the “Origin” column of incident reports, with United States leading the list. We see similar trends in our production telemetry, as explained later.
Telemetry detections
To confirm these findings, we wanted to validate using another data source. We reviewed our telemetry from Bitdefender endpoint security agents, collected between December 11th and December 15th.
Many customers are launching simulated attacks against their own network to identify vulnerable systems. To compensate for this, we have filtered this data and tried to identify regular penetration attempts and security scans. We have excluded 75% of detections that seem to originate from companies testing their own networks (this high rate of exclusions is a good sign, because it means that security teams are taking this threat seriously.)
The graph below represents the top 10 countries where attacks originated from during the observation period. 80% of the attempts have originated from these 10 countries. Germany leads the list with a significant percentage of attacks coming from United States and Netherlands as well.
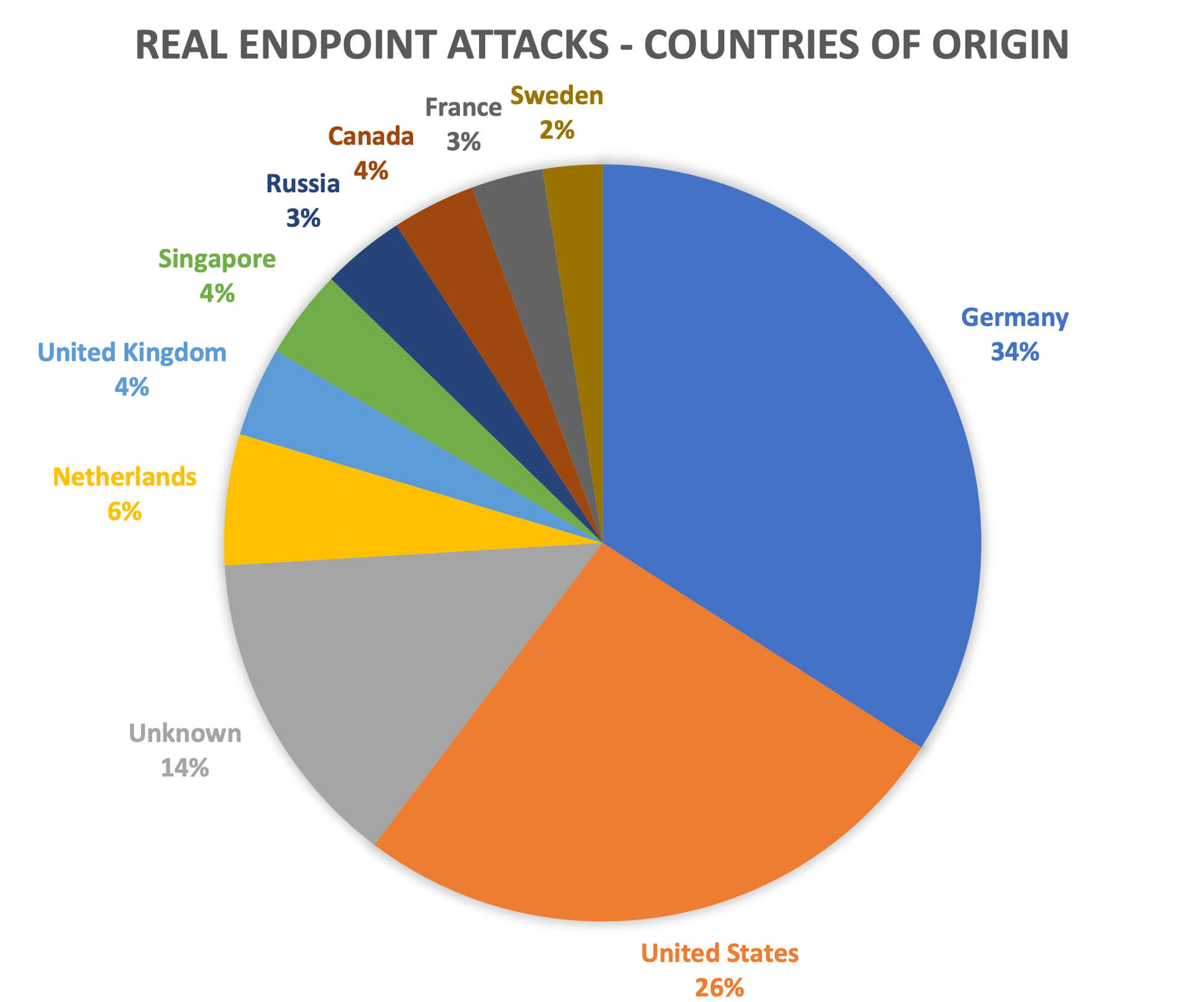
Top 10 countries where Log4j infiltration attempts originated
The list of intended targets, however, is not so surprising – leading with United States, Canada and United Kingdom. In the telemetry, we detected attacks against 105 countries, but 67% of all attacks targeted these 10 countries.
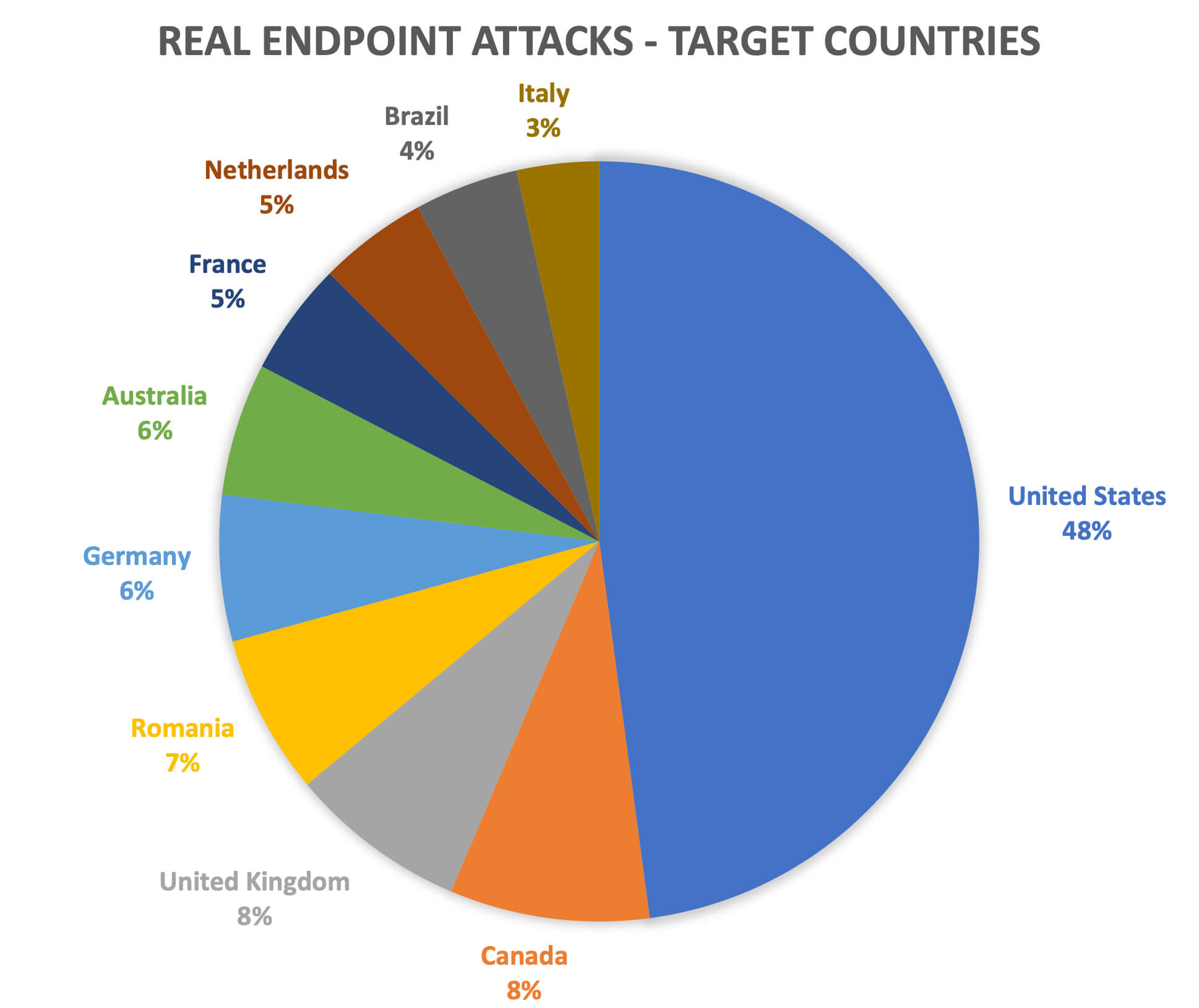
Top 10 countries that were targeted
In our telemetry, we are seeing various security modules preventing different stages of attacks from fully expanding. From network protection (URL/IP reputation), static antimalware (detecting miners or known malicious payloads), Advanced Threat Defense for detecting suspicious process behavior, and EDR for detections of reverse TCP shells and anomalies. The defense-in-depth approach is a proven strategy that helps prevent security incidents from becoming security breaches and here we see this playing out with log4j.
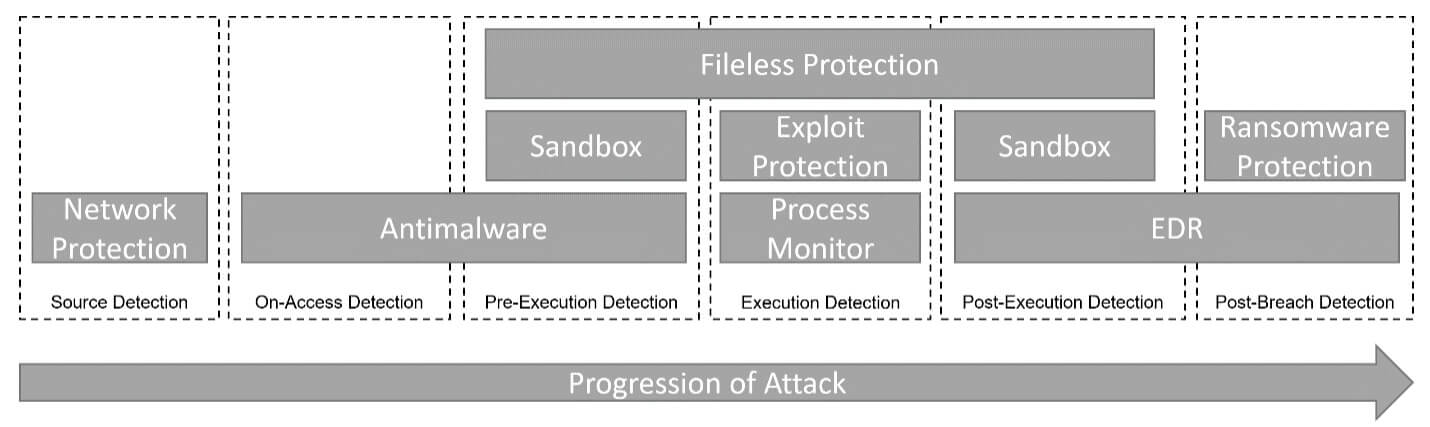
Different stages of prevention and detection
What’s next
It is important to note this is a highly dynamic situation and continues to develop. Mitigating, or even understanding the impact of this vulnerability, is going to take months and this is a perfect window of opportunity for various threat actors.
We haven’t detected any activity from a known Ransomware-as-a-Service gang or APT group yet, but this is an ideal opportunity for these professional threat actors to establish a foothold for later exploitation. We are continuously monitoring for their presence because we anticipate professional threat actors with long-term (or high value) exploitation plans will use this opportunity to plant a backdoor, quietly patch the vulnerability to prevent other threat actors from interfering (and hiding the affected machine from internal vulnerability scanning) and wait for the initial storm to pass before launching their attack. To maximize the pressure on victims, threat actors will probably wait until Christmas or the end of year to launch their attacks.
We are continuously monitoring the darknet activity and see a lot of interest in this vulnerability.
A video from Invidious – a darknet video streaming platform, similar to YouTube. As of 12/16/2021, this video has 200K+ views and almost 1500 comments.
What should you do now? Follow the guidelines in our prior Security Advisory and Technical Advisory articles and continue to actively monitor your infrastructure for potential exploitation attempts in order to respond accordingly. Now is always a good time to make sure your business is more cyber resilient, and your security team is prepared to detect and respond to potential intrusions.
