2021 Gartner® Market Guide for Cloud Workload Protection Platforms | Bitdefender’s key takeaways from the report

Protection requirements for cloud workloads continue to grow as organizations accelerate their adoption of containers and host an ever-increasing number of workloads in hybrid and multi-cloud architectures. Cloud Workload Protection Platforms (CWPP) are critical to protect these workloads from cyberattack and provide security teams with visibility into, and control of, cloud-based infrastructure and applications.
In the new 2021 “Market Guide for Cloud Workload Protection Platforms” report, Gartner highlights the latest developments, key findings and recommendations that enterprises should consider to protect their workloads from the latest cyberthreats. Read the report to understand:
- Best practices for securing cloud-native applications and hybrid cloud environments
- Analysis of CWPP controls and different solution types
- Evaluation criteria for CWPPs and cloud security strategy recommendations
Bitdefender is positioned in this report by Gartner as a representative vendor for CWPP.
What is a CWPP ?
According to Gartner, “CWPPs are workload-centric security products that protect server workloads in hybrid, multi-cloud data center environments. CWPPs provide consistent visibility and control for physical machines, virtual machines (VMs), containers and serverless workloads, regardless of location.”[1] CWPP offerings include a combination of prevention, monitoring, system protection and application control.
Why is cloud workload protection important for my business?
Digital transformation and cloud adoption trends accelerated dramatically in 2020 as organizations transitioned to a remote workforce and increasingly moved on-premises workloads to the cloud. This move to the cloud has opened new security challenges and vulnerabilities not seen in traditional perimeter-based security. raditional endpoint protection platforms (EPP) are typically not up to the unique security requirements of cloud workloads with the Gartner reporting stating, “Enterprises using endpoint protection platform (EPP) offerings designed to protect end-user devices for server workload protection are putting their data and applications at risk.”[2]
In a recent Gartner survey[3], “76% of enterprises indicated they are using multiple infrastructure as a service (IaaS) provider.” Why is this? By moving to this model, companies can protect more of their workloads (on-site and cloud based) while reducing security risks by diversifying their business – similar to stock portfolios. This process is also called a hybrid or multi-cloud architecture which an effective CWPP should be capable of addressing. With the implementation of CWPPs, companies can proactively protect these cloud assets instead of waiting to react once an attack has already occurred.
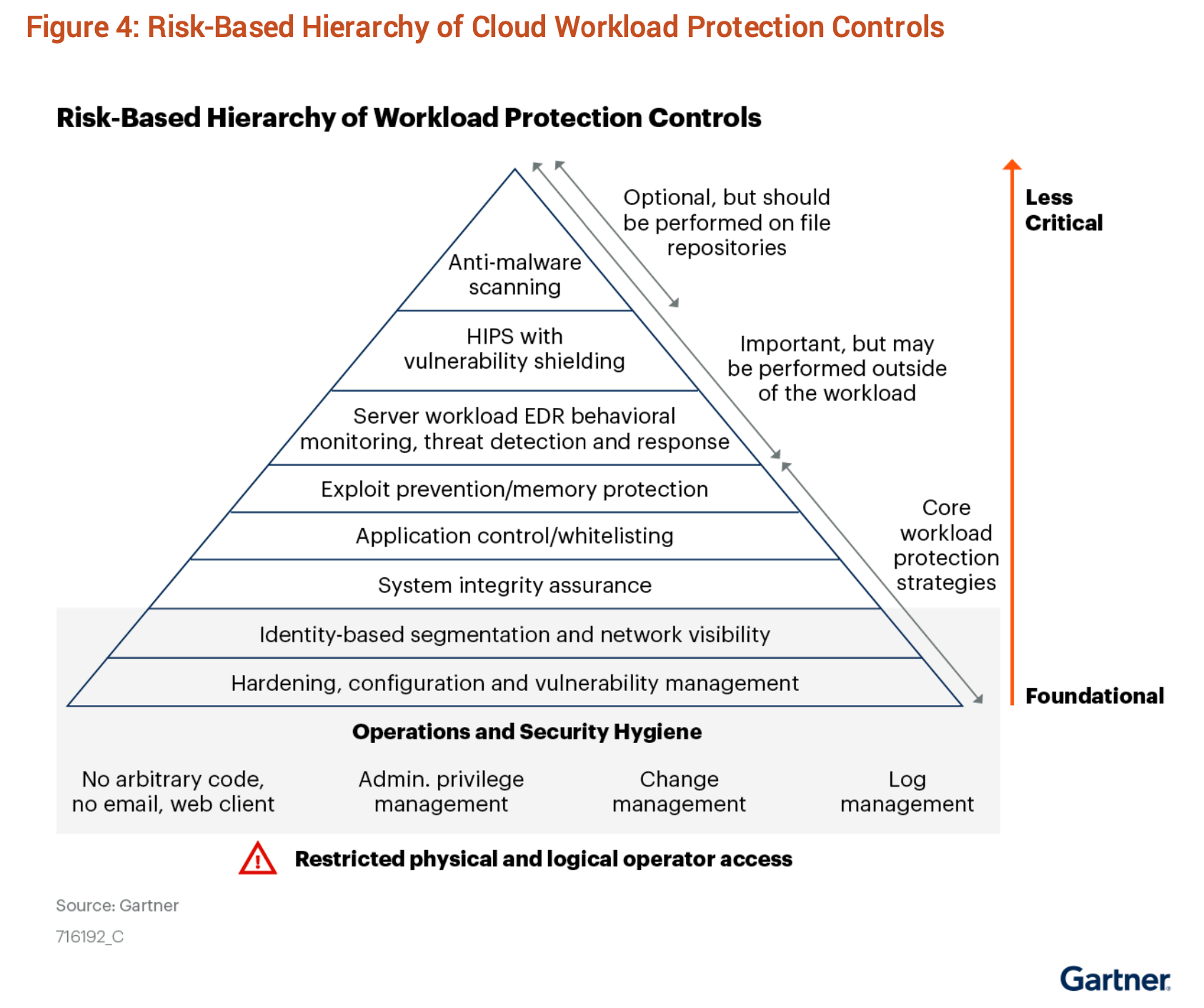
Shown in the model above, companies who leverage a CWPP for their cloud infrastructures can integrate numerous security capabilities into their workloads. These critical security features include – vulnerability management, compliance, runtime protection and application control, and other key security controls highlighted by Gartner.
Key takeaways from Bitdefender on Gartner Market Guide for Cloud Workload Protection Platforms
The Gartner Market Guide for Cloud Workload Protection Platforms report is a valuable resource for security and DevOps professionals as they look to identify key trends, recommendations and vendors. Some of the areas of interest we identified as key takeaways include:
- “Workloads are being moved from on-premises to public cloud IaaS, and the overall number of IaaS workloads (including containers and serverless functions) is growing rapidly.”
- “Modern digital business applications and services are composed of multiple workloads (units of back-end compute work) running on-premises and also in IaaS. In a recent Gartner survey, 76% of enterprises indicated they are using multiple IaaS providers.”
Our takeaway: Organizations are now leveraging distinct technology stacks for individual use cases more so than ever. This results in technology fragmentation with different IaaS and PaaS usage throughout a single organization. We agree with Gartner’s point of view and further believe that a holistic solution which provides a single security platform for eXtended Endpoint Detection and Response (XEDR) and Managed Detection and Response (MDR) across traditional, cloud and hybrid cloud is necessary for hybrid cloud workload protection. Minimizing operational overheads and risk regardless of technology choices made by teams.
- “The rapid adoption of Kubernetes. Kubernetes has emerged as the de facto standard for Linux container orchestration. Some startup CWPP vendors focus only on securing Kubernetes environments. Support for Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform (GCP) managed Kubernetes services is a common requirement, along with support for IBM Red Hat OpenShift.”
Our takeaway: We recognize that organizations have many options for orchestrating and hosting their containers, and that customers use various platforms and technologies across their business. The flexibility to use the right technologies to support each application use case drives innovation and enables a fast time-to-market. On the other hand, robust and effective security requires a holistic approach to ensure timely detection of threats and minimize operational overhead. Organizations need a security solution that works in many environments, providing a path of least resistance for security teams, regardless of the choices made in delivery and infrastructure parts of the organization.
Ultimately container architectures come in a variety of flavors which necessitates a solution that is built for the specific purpose of securing containers. Most security vendors have either retrofitted old technology or focused on only one flavor of container hosting, restricting innovation and flexibility of technology choices.
- “Requests from enterprises for workload threat detection and response capabilities. Organizations that adopt Gartner’s continuous and adaptive risk and trust assessment (CARTA) strategic framework and a zero-trust security architecture acknowledge that CWPP strategies cannot rely solely on preventive controls. Thus, server workload behavioral monitoring (endpoint detection and response [EDR] for servers) is becoming a critical requirement of CWPPs.”
Our takeaway: Even with the best security hygiene practices, one cannot prevent 100% of attacks. Monitoring of applications and systems during runtime can reduce the risk of a breach to a minimum through a combination of risk-based security and attack detection and response.
Recommended next steps for protecting your cloud workloads
We concur with Gartner that the shift to cloud-native application development using container-based application architectures requires new CWPP capabilities both for development and at runtime. This is why we built Bitdefender GravityZone Security for Containers from the ground up to ensure the best possible experience for customers.
Bitdefender GravityZone Security for Containers extends Bitdefender’s cloud workload security offering to protect customers across traditional, cloud and hybrid cloud workloads, to stop attacks early in the kill chain with advanced anti-exploit and advanced machine learning analytics technologies.
Once you’ve decided which CWPP solution is the best fit for your business, learn how to protect and transition your company to a cloud-first organization using our Best Practices for Cloud Workload Protection.
This complimentary report is provided by Bitdefender.
[1,2,3],Gartner “Market Guide for Cloud Workload Protection Platforms,
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
GARTNER is a registered trademark and service mark of Gartner, Inc. and/or its affiliates in the U.S. and internationally, and is used herein with permission. All rights reserved.
