NSA Offers Sysadmins Guidance on Eliminating Obsolete TLS Configurations

The US National Security Agency (NSA) has released a security advisory warning network administrators and security analysts that “new attacks against Transport Layer Security (TLS) and the algorithms it uses have been discovered.” Primarily aimed at government entities, the notice instructs IT admins to “make a plan on how to weed out obsolete TLS configurations in the environment by detecting, prioritizing, remediating, and then blocking obsolete TLS versions, cipher suites, and finally key exchange methods.”
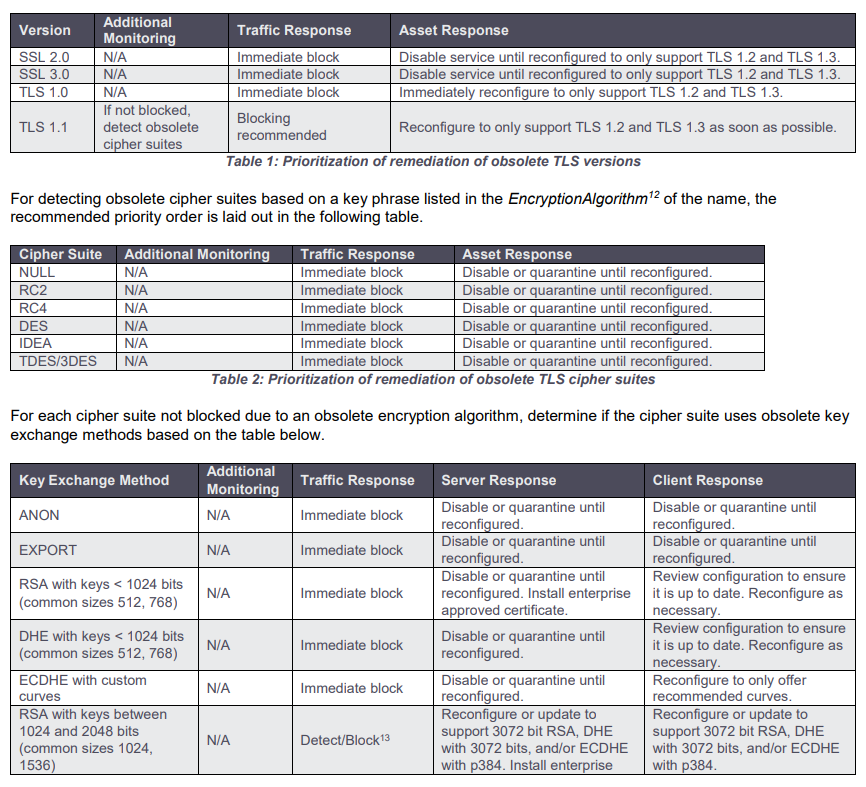
The guidance details recommended detection and remediation strategies and points out the exact TLS configurations that admins should stop using.
For example, NSA recommends that only TLS 1.2 or TLS 1.3 be used, and that SSL 2.0, SSL 3.0, TLS 1.0, and TLS 1.1 not be used. And even when TLS 1.2 and TLS 1.3 are employed, NSA recommends that cryptographic parameters meet the algorithm requirements in CNSSP 15, referred to as Commercial National Security Algorithms.
“Detecting systems that negotiate obsolete TLS versions or cipher suites or use weak keys is a first step that will help prioritize remediations,” the agency notes. “Once detected, an organization’s servers and clients negotiating obsolete TLS sessions should be reconfigured to meet the requirements of CNSSP 15.”
NSA offers administrators full configuration information at github.com/nsacyber/Mitigating-Obsolete-TLS.
The document also includes tables listing the prioritization and urgency for immediate remediation of obsolete TLS versions.
“Using obsolete TLS configurations provides a false sense of security since it looks like the data is protected … Prepare for cryptographic agility to always stay ahead of malicious actors’ abilities and protect important information,” the agency adds.
