On February 19, 2024, ConnectWise released a security patch addressing two vulnerabilities in the ScreenConnect software, potentially leading to Remote Code Execution (RCE). These vulnerabilities, identified as CVE-2024-1709 and CVE-2024-1708, allow attackers to bypass authentication and perform path traversal, respectively, enabling unauthorized access and administrative privilege escalation.
Vulnerability Details
- CVE-2024-1709 (CVSS 10.0) – Authentication Bypass using an alternate path or channel (CWE-288)
- CVE-2024-1708 (CVSS 8.4) – Improper limitation of a pathname to a restricted directory aka “path traversal” (CWE-22)
The attack complexity is low, and it does not require any privileges. While not all technical details are known yet, one way to exploit this vulnerability is by appending a string after /SetupWizard.aspx to gain access to the setup wizard on a previously configured system. This enables a threat actor to add a new administrative user. Multiple Proof of Concepts (POCs) are already available, and it has been confirmed that this vulnerability is actively exploited.
To contribute to the security community’s understanding of the current threat landscape, we’d like to share additional insights from our telemetry and analysis. We’ve noticed several instances of potential attacks leveraging the extensions folder of ScreenConnect located at %ProgramFiles(x86)%\ScreenConnect\App_Extensions. While it was previously reported by Huntress that this location could be exploited for file uploads in the root of the folder, our observations suggest the use of regular extensions. While we lack access to these files for a thorough analysis, the triggered detection (Generic.Cert.Downloader.1) suggests the presence of a downloader based on the certutil.exe built-in tool. Threat actors commonly employ this tool with the -urlcache or -f arguments, to initiate the download of additional malicious payloads onto the victim’s system. Considering the timing and the format of randomly generated filenames, these attacks could be based on one of the published POCs. Below is a list of available indicators of compromise:
- %ProgramFiles(x86)%\ScreenConnect\App_Extensions\f74712f2-7944-cb0e-6f6c-ca90d2c8ca18\iyrretkg.ashx (MD5:f052b0a702854a601741e7034d75d883)
- %ProgramFiles(x86)%\ScreenConnect\App_Extensions\ab75a33c-f8eb-aaab-93de-f92cc16eca81\nsrtxeav.ashx (MD5:cff3433c3eff1f20f883ef7d8c662a1a)
- %ProgramFiles(x86)%\ScreenConnect\App_Extensions\5b8f5ca4-b477-5f91-dd41-9b228a68f6a5\exirjllq.ashx (MD5:a2230883a1a3b6c93ee5fd207455c46e)”
Recommendations
- Patch Management
- Immediately apply the security fix provided by ConnectWise to mitigate the vulnerabilities. On-premises versions up to and including 23.9.7 are vulnerable.
- ConnectWise has removed license restrictions for this release, enabling partners without active maintenance to upgrade to the latest version of ScreenConnect.
- Auditing and Monitoring
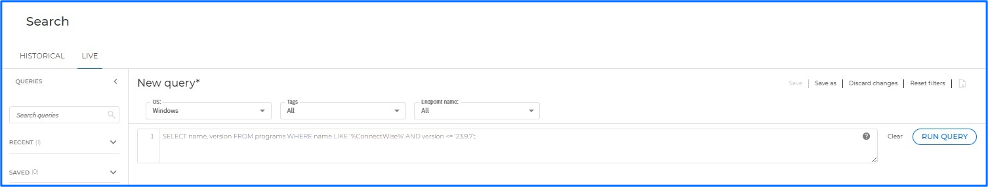
- Conduct a thorough audit to identify all systems where ConnectWise ScreenConnect is deployed. Use the GravityZone platform’s Live Search query feature to locate vulnerable versions of ConnectWise services: SELECT name, version FROM programs WHERE name LIKE ‘%ConnectWise%’ AND version <= ‘23.9.7’;
- Monitor the C:\Program Files (x86)\ScreenConnect\App_Extensions\ folder for any suspicious .ashx and .aspx Files stored directly in the root of this folder may indicate unauthorized code execution.
- For Bitdefender MDR customers, our Security Operations Center (SOC) team conducts threat hunting based on known Indicators of Compromise (IOCs) collected by our cyber threat intelligence team.
- Detection and Response
- Implement robust detection and response capabilities to identify and respond to potential exploitation attempts.
- Bitdefender GravityZone XDR sensors can detect suspicious activity and alert security teams to unauthorized access or lateral movement attempts.
Augment security operations with managed services like Bitdefender MDR to enhance threat detection and response capabilities.