
In the third and last part of the blog series on Practical Cyber Resilience, I will cover the Approaches, Tactics and Techniques that an organization should use when developing options for improving cyber resilience. In the previous blog, I detailed the practical five-step Cyber Resilience Analysis Process recommended both by NIST and MITRE for enhancing cyber resilience.
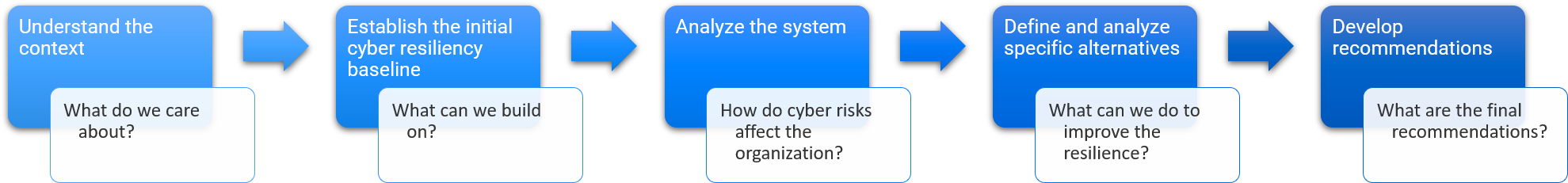
The fourth step of the Cyber Resiliency Analysis is centered on/around identifying specific ways to make desired improvements. These alternatives include implementing cyber resiliency techniques (such as Adaptive Response or Analytic Monitoring) in the context of the existing architecture but may also involve significant changes to the security architecture if needed. The potential solutions can be purely technical, purely procedural, or combinations of the two.
The NIST framework provides a wealth of details on how cyber resilience techniques translate into cyber resiliency approaches. A cyber resiliency approach is a subset of the technologies and processes that defines how the capabilities are implemented or how the intended consequences are achieved.
Let us take an example of how to identify potential solutions for increasing resilience. Let’s assume that during the cyber risk baselining phase we identified Analytic Monitoring as an area of high importance with significant room for improvements. To help defining improvement options, the NIST framework provides three corresponding resiliency approaches for this technique: Monitoring and Damage Assessment, Sensor Fusion and Analysis plus Forensic and Behavior Analysis. The three approaches translate into:
- Monitoring and analyzing the behavior and characteristics of components and resources. This helps improving the ability to detect indicators of attacks and for assessing the potential damages.
- Combining and analyzing data, collected from different information sources over extended timeframes, to provide visibility and insights.
- Analyzing the attacker tactics, techniques, and procedures (TTPs), including malware and other artifacts left behind by security events. This provides better understanding of the impact and helps guiding the response actions.
Having these directions set, let’s shift to identify technical solutions. Contrary to the initial instinct of most security practitioners, the best time for choosing security technologies is near the end of the cyber resiliency analysis process. Making technology choices too early often leads to spending resources on technology that is not effective in the context of the overall scope of increasing resilience. Or it leads to missing the chance to allocate resources where they matter the most.
For our example, you can probably recognize that some of these capabilities described above fall within Endpoint Detection and Response solutions. EDR is an excellent choice for implementing Analytic Monitoring especially for endpoints (physical or virtual). It enables monitoring of events across all endpoints in the infrastructure, strong analytics capabilities, and detailed incident investigation to get a clear picture of adversarial TTPs.
What (pure) EDR is missing in the context of the Analytic Monitoring cyber resilience technique, is the sensor fusion (EDR is focused on endpoint only). However, EDR is expanding to include data from other infrastructure elements: like network and email. This is the eXtended Detection and Response (XDR) solution. XDR provides detection and response capabilities for a much larger area of the enterprise infrastructure and scores well for Analytic Monitoring cyber resilience technique. In the case of our example, it is a good technology to consider.
As mentioned, enhancing cyber resilience may require both adding/replacing technology and changing processes. An organization could build the corresponding processes for analytic monitoring in-house or outsource to a third party. For operating an EDR/XDR solution, an enterprise should have an internal security operations team but may also consider using Managed Detection and Response (MDR) as an alternative. MDR includes both the technology and high-level security expertise to deliver security outcomes that map directly to cyber resilience objectives.
This example provides just one option for implementing the Analytic Monitoring cyber-resilience technique. An organization should always consider multiple alternatives and feed them into the last step of the Cyber Resilience Analysis process – that is value of using the framework. Solutions will be assessed in the light of the larger context to identify the best recommended course of action. This process should be repeated and applied regularly to keep pace with cyber resiliency needs as the threat landscape continues to evolve.
Wrapping up the series, the three blogs covered some important practical aspects to consider for enhancing the cyber resilience of the organization. In the first blog I covered the four key characteristics (or guiding principles) of cyber resilience while in the second I reviewed the main objectives and the five-step Cyber Resilience Analysis methodology. The last part was dedicated to how an organization should approach the task of identifying the best solutions to apply for enhancing the resilience of the organization when faced with common and advanced cyber threats.