
An app which purported to launch distributed denial-of-service (DDoS) attacks against the internet infrastructure of Russia, was in reality secretly installing malware on to the devices of pro-Ukrainian activists.
As researchers at Google’s Threat Analysis Group (TAG) describe, the Moscow-backed Turla hacking group created a website purporting to belong to Ukraine’s Azov regiment.
On the bogus website, users were encouraged to download a tool that would allegedly swamp Russian websites with unwanted traffic.
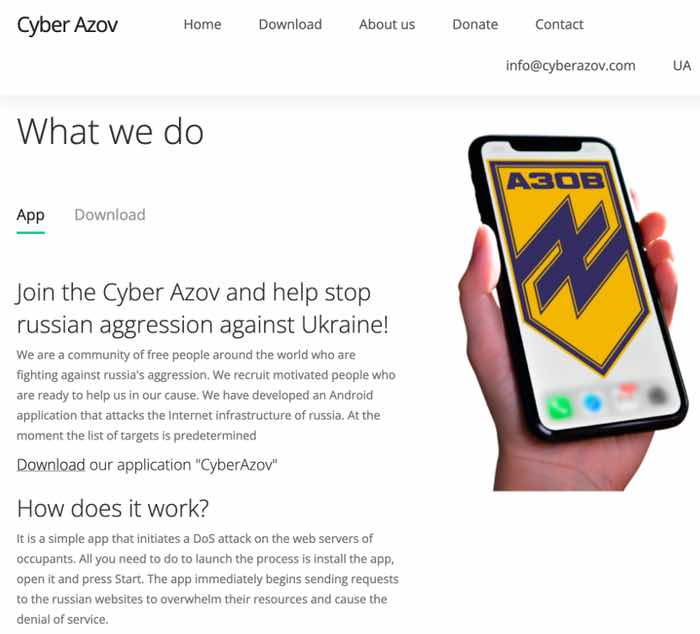
The website claimed to explain how the app, which was not available on the official Google Play store, would help in the fight against Russia’s invading forces:
It is a simple app that initiates a DoS attack on the web servers of occupants. All you need to do to launch the process is install the app, open it and press Start. The app immediately begins sending requests to the russian websites to overwhelm their resources and cause the denial of service.
To anyone who didn’t look closely, the app’s website might appear not dissimilar to that belonging to the StopWar Android app, that bombards Russian sites with traffic.
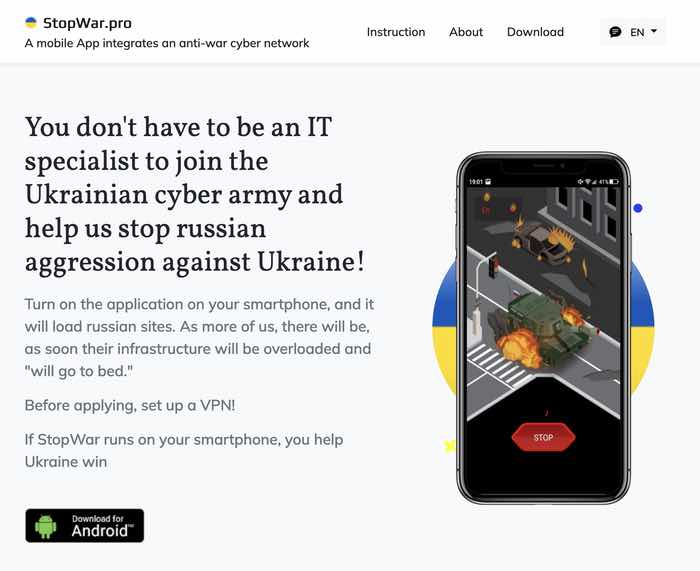
Would you be able to easily tell one app from the other based on these websites?
Because there’s a fundamental difference between StopWar and the so-called “Cyber Azov” app.
According to Google’s researchers, the Cyber Azov app only visits the Russian websites it claims to be attacking once, in an apparent attempt to gather information about those pro-Ukraine activists who would be tempted to use such a tool.
The good news is that the researchers do not believe that many people were duped into downloading the bogus Cyber Azov tool, even though links to it were disseminated via messaging services in an attempt to seed the app amongst activists fighting the Russian invasion.
The war in Ukraine has seen both sides of the conflict mobilising hackers.
The FSB-backed Turla group (also known as Waterbug or Venomous Bear), for instance, has been involved in a wide range of activities including targeted APT attacks against government organisations, spear phishing, and cyberespionage.
Turla’s bogus DDoS tool may not have amounted to much of a serious threat, but it is clear that other attacks launched by the group in the past have been successful… and no doubt they will be again.