
Cloud security researchers have discovered a flaw in Microsoft’s Azure App Service that exposed source code for at least four years. There is strong indication that bad actors are exploiting the flaw on unsecured configurations.
Wiz.io researchers have found “insecure default behaviour in the Azure App Service that exposed the source code of customer applications written in PHP, Python, Ruby, or Node, that were deployed using ‘Local Git’,” according to a responsible disclosure by the cloud security outlet.
Dubbed NotLegit by the researchers, the flaw basically allows a user to unintentionally configure the .git folder to be created in the content root, “which puts them at risk for information disclosure,” according to Microsoft’s own disclosure.
“This, when combined with an application configured to serve static content, makes it possible for others to download files not intended to be public,” according to the Windows maker.
Wiz reported the flaw on Oct. 7 and Microsoft has since taken steps to mitigate the issue. However, customers could still be exposed and are advised to take the steps needed to protect their applications, as detailed in Microsoft’s email alerts issued between Dec. 7 and Dec. 15 (pictured below).
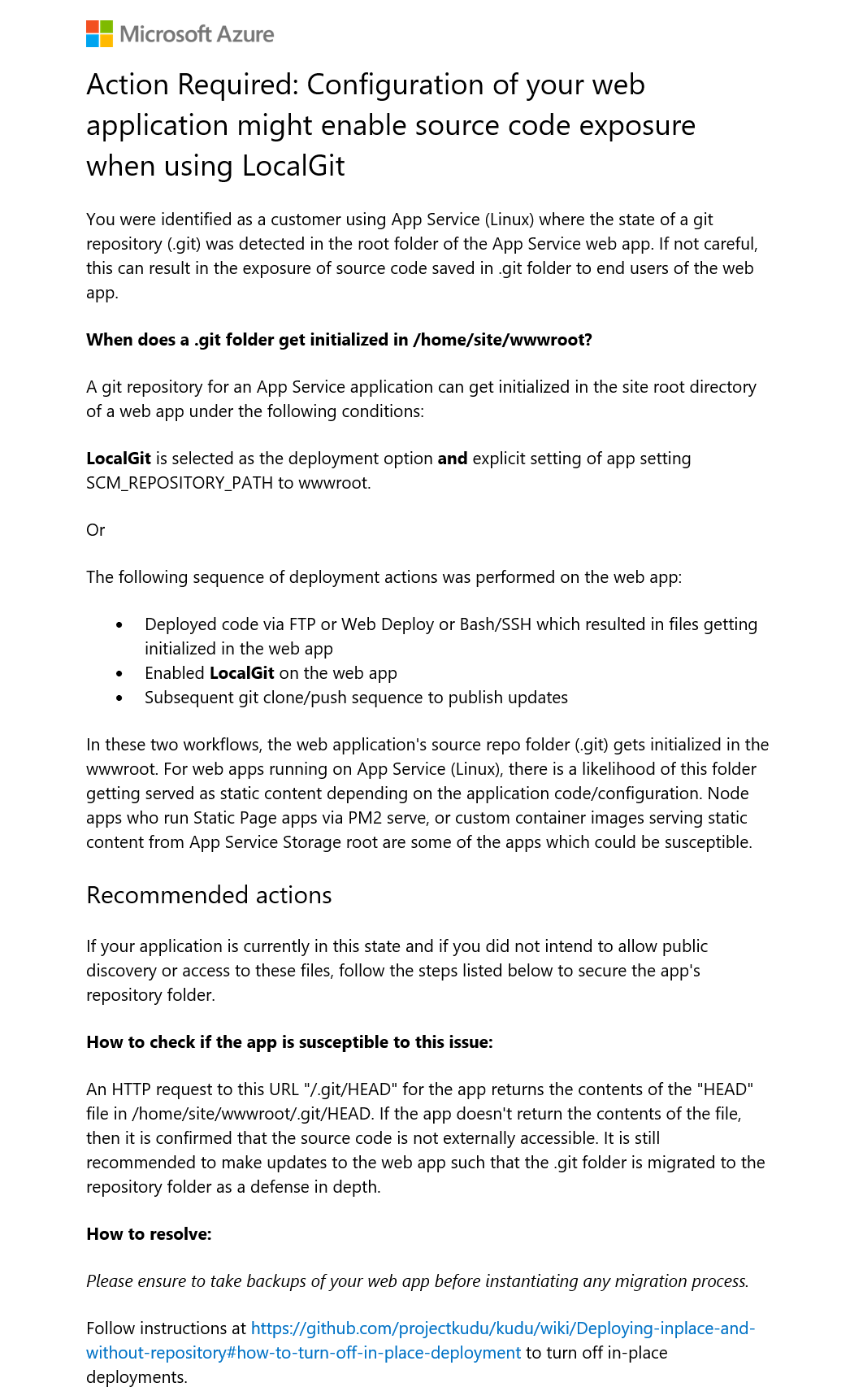
The Redmond-based software giant commends Wiz’s responsible disclosure and help in securing customers before going public with the findings.
Notably, the research team took extra steps to assess the chance of exposure and deployed a vulnerable Azure App Service application linked to an unused domain to see if anyone tries to reach the goods inside the .git folder.
Within four days of setting the bait, the honeypot registered multiple requests for the .git folder from unknown actors, the team said.