
The Cybersecurity & Infrastructure Security Agency (CISA) and the National Institute of Standards and Technology (NIST) this week released an overview of supply chain threats. Its purpose: to help organizations keep themselves out of scenarios like the recent SolarWinds incident.
The 16-page Defending Against Software Supply Chain Attacks released by CISA and NIST this week provides an overview of software supply chain risks and recommendations on how software customers and vendors can use the NIST Cyber Supply Chain Risk Management (C-SCRM) Framework and the Secure Software Development Framework (SSDF) to identify, assess, and mitigate software supply chain risks.
The resource provides in-depth recommendations and key steps for prevention, mitigation and resilience of software supply chain attacks like the widely circulated hack on SolarWInds’ IT management platform, Orion.
“A software supply chain attack—such as the recent SolarWinds Orion attack—occurs when a cyber threat actor infiltrates a software vendor’s network and employs malicious code to compromise the software before the vendor sends it to their customers. The compromised software can then further compromise customer data or systems,” CISA explains.
“Newly acquired software may be compromised from the outset, or a compromise may occur through other means like a patch or hotfix. In these cases, the compromise still occurs prior to the patch or hotfix entering the customer’s network. These types of attacks affect all users of the compromised software and can have widespread consequences for government, critical infrastructure, and private sector software customers,” the agency adds.
The document outlines how supply chains fit within the greater information and communications technology (ICT), and how software is at risk of malicious or inadvertent introduction of vulnerabilities at each phase of the ICT supply chain lifecycle. The diagram below offers several examples of supply chain attacks over the years.
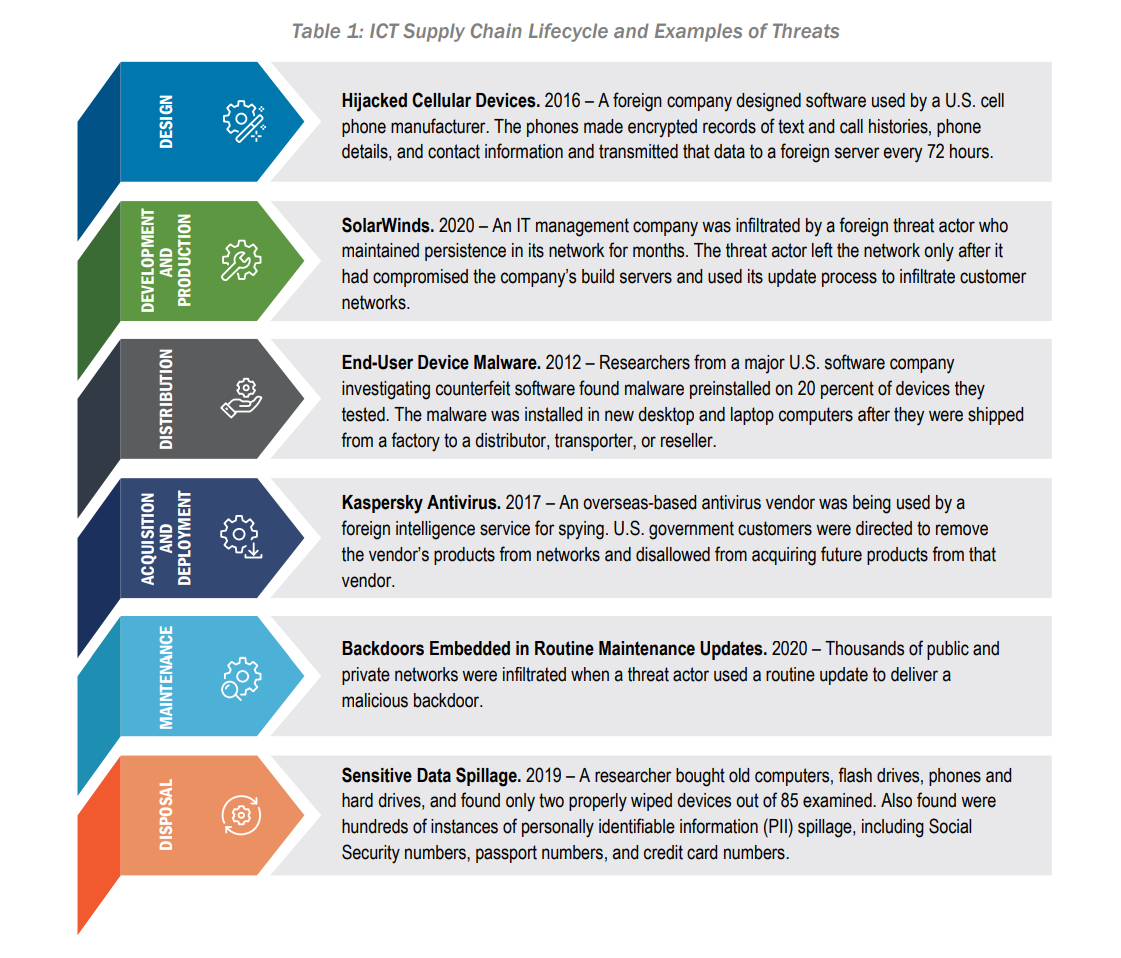
CISA strongly encourages IT administrators in both camps – vendors and customers – to review Defending Against Software Supply Chain Attacks (PDF) and implement its recommendations.