
It’s been more than one year since people around the world were forced into technology, whether they liked it or not. Governments, healthcare providers, restaurants and the rest have flooded users with applications to help them safely get in touch with the outside world.
In this context, cybercriminals have rapidly adapted their strategy to capitalize on this newly opened market and trick victims into installing malicious apps on their Android phones. Bitdefender researchers have found multiple apps taking advantage of mobile users looking for information about the vaccines or seeking an appointment to get the jab. We expected this phenomenon after spotting a campaign a year ago when COVID-19 had just struck and users were restlessly looking for information.
Campaigns using COVID-19 vaccines as a pretext to deploy malware are a global problem, and they range from annoying but seemingly innocuous apps packed with adware to fully fledged Banker Trojans ready to take over the device after just a few taps.
One of Android’s main strengths, and weaknesses at the same time, is the user’s ability to sideload apps. This feature lets people load apps that are not available in the official store. Unfortunately, it also means many users unintentionally load malware from third party-stores or locations.
While this is a serious problem, the malware-ridden apps we’ve found are not limited to third-party locations. Some are still available through Google Play, despite Google’s efforts to weed out malicious apps during the developers’ uploading process.
Hydra Bankers
Two of the samples we’ve identified are part of the infamous Hydra trojan family. Historically, Hydra targeted Turkish users , but lately it has been extending its reach. This time its chosen victims are from Chile and other Spanish-speaking countries.
| APK MD5 | af2e61a6778c3a3a1001f87ea9c96e80 | 56d07c9e9747c63ad8ee03a46fc5d26d |
| Icon |  |
|
| Package name | uniform.despair.grass | ball.ridge.fly |
| CnC | shabukenkeinside.com | |
| Distributed as | Vacuna_COVID19_Chile.apk | |
| Application name | Vacuna Covid-19 Chile | |
| Translated Label | Vaccine Covid-19 Chile | |
| Translated Icon | Ministry of Health, Government of Chile |
Both applications try to pass themselves off as a Coronavirus vaccine app for users based in Chile, and their behavior is very similar. One of the versions has been mentioned before on Twitter.
Users were able to download the apps from the following domains. Both domains resolved IP belongs to a web hosting provider from Malaysia. . As of the moment of writing, the domains have stopped serving the malware.
| Distribution Point | IP | Registration Date | Expiration Date |
| Miinsaludgovcovacunacovid[.]com | 111.90.145.231 | 12.02.2021 | 12.02.2022 |
| miinsalud-gov-cl-vacuna-cvid19[.]com | 111.90.145.231 | 15.02.2021 | 15.02.2022 |
Once the victims open the app, they try to lure them into activating the Accessibility permission for the app. If the user accepts, the application moves on to giving itself all the permission it requires, hides its launcher, and sends a premium SMS message. The premium SMS role is likely simple — to verify whether the malicious apps have acquired the necessary permissions.
The Accessibility permissions let the apps inspect the window’s content and collect data such as credit card numbers, passwords and more. From there, it’s only a matter of time before the user’s banking data is leaked.
The user can’t disable the Accessibility permissions or uninstall the app, since the app automatically redirects them to the home screen.
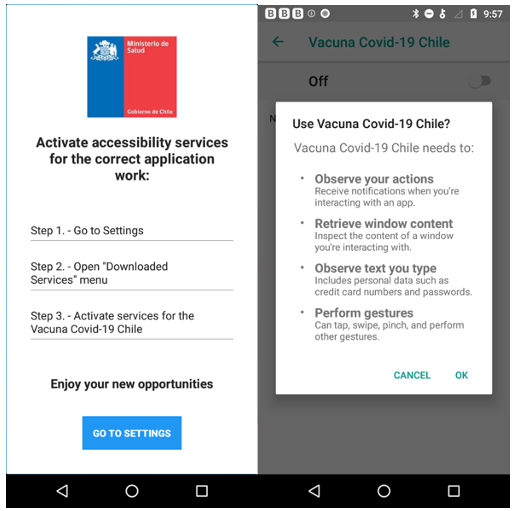
The samples we collected show zip file dates of 2021.02.12 and 2021.02.15, respectively. It seems their corresponding distribution points were registered the day they were built. Although these timestamps are no guarantee of an exact build time, they hint at the beginning of the attack.
The way criminals distribute this malware shows that they target Spanish speakers. Also, malicious Banker Trojans usually come with a list of banking applications they are targeting. All targets of the 30 different apps are financial applications with mainly Spanish speaking users (readers can see the complete list of applications in the Indicators of Compromise section).
Our telemetry readings show that the threat is currently active, predominantly in Spain. We detect this threat as Android.Trojan.Banker.RY.
Cerberus Bankers
The other banker family we have found taking advantage of the coronavirus vaccine is the well-known Cerberus malware-as-a-service. One of the apps shows a zip file date of 26.01.2021. It didn’t take these malware actors too long to jump on the Coronavirus vaccine bandwagon.
| APK MD5 | 0da756d28cead23b2c0e09573b2467ee | 53550f69f2eecd26910fead5748e094b |
| Icon |  |
 |
| Package name | com.aivjutzyceew.jgiriaeg | com.lgiueovx.xlfhh |
| Distributed as | Asi_Sorgu.apk | Asi_Takip_Sistemi.apk |
| Application name | AşıSorgu | AşıTakipSistemi |
| Translated Label | Vaccine Query | Vaccine Tracking System |
| CnC | 193.37.212.151 | mohabmnho.surf |
The malware attempts to spoof known legitimate Turkish healthcare apps that can be currently found on Google Play. For example, the ATS AşıUygulama (icon to the right).
The Cerberus family has been largely documented and, behavior-wise, these applications stick to the pattern.
After the user’s first tap to open the app, the apps will request the Accessibility permissions until the user grants them. The apps will keep popping up and display ‘toast messages’ until the user caves in and accepts the request. Toast messages are small snippets of text displayed on the screen. Once the victims grant the malware the requested Accessibility permissions, the apps hide their launcher and proceed to take over the device.
Both samples found target Turkey, as inferred from the application name:
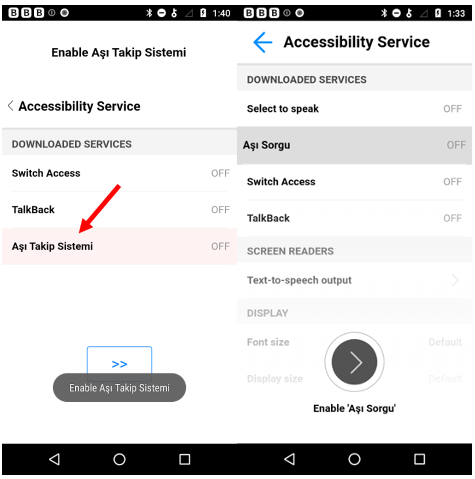
We detect this threat as Android.Trojan.Banker.UI.
Repackaged adware
Many legitimate informational apps regarding the coronavirus vaccine have appeared in the last couple of months. Vaccinum is one of them. It was initially an application meant to provide users with advanced statistics on the vaccination status on a national and global level. However, its initial purpose made it a perfect target for malware creators.
The original application was available on Google Play for a while before the app store’s Covid-19 related regulations [6] required its developers to take it down. Currently, if users visit the app’s official website, they will find the following message:
While Google Play has legitimate reasons to add restrictions to Covid-19-related applications, deleting apps may lead some users to turn to other third-party Android application markets that tend to be more lenient when it comes to unwanted content.
This is where we find a new version of Vaccinum. While this version is the same as the original app functionality-wise, it comes repackaged with adware.
| Code of last known original (clean) version | Code of repackaged version with ads 93d7b7ba67c51d60a616fad011da0110 |
 |
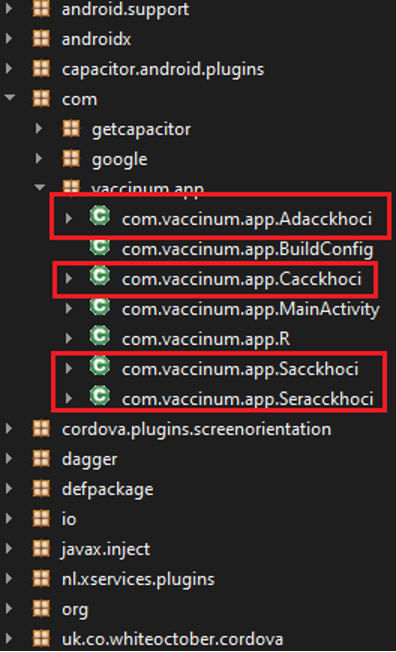 |
Every time a user opens the modified app, a pop-up appears after a couple of seconds with an advertisement and a request from a site to send notifications to the device. The ad also has a “SKIP AD” button that does nothing despite its name. It simply opens a different ad in the browser. The host site requests to send notifications, after which the website attempts to scam the user.
In this example, the website tries to persuade the victim to send a text message to a short code.
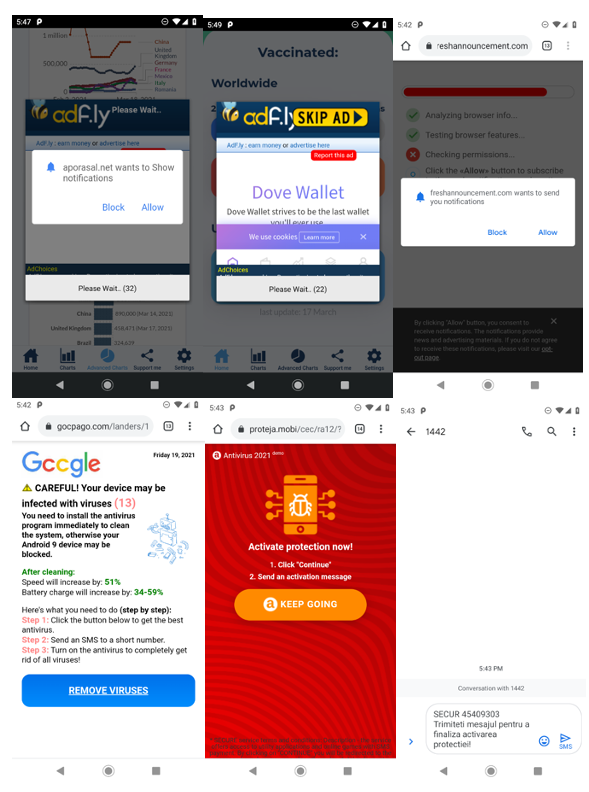
We detect this threat as Android.Adware.Agent.BMI.
Co-Win Adware
The Indian government launched a COVID-19 vaccine tracking and registration platform, Co-Win, on March 1, 2021. Reports of malware imitating Co-Win and of bad actors copying other Indian healthcare apps quickly emerged. Adware and fake applications immediately followed. The Indian government issued a warning in this regard.
Despite the official warning, we have observed more adware arriving in the official Google Play store. Google has been trying to vet all vaccination-related applications properly, but some fell through the cracks.
An application named “Guide for Co-Win India App – Made In India” (with a package name of register.guidefor.cowin20), that also takes advantage of India’s Covid vaccine registration system, Co-Win, is the perfect example of an app that shouldn’t exist in the official store.
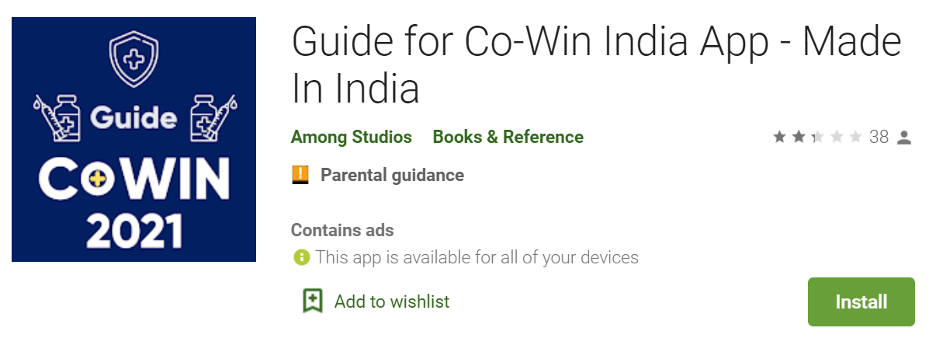
Our systems indicate that this app has been active on Google Play since the middle of January, at least. The app attempts to provide information on how to use the Co-Win system. However, the app bombards its users with advertisements.
This application comes with a disclaimer: “This app is not official app of any government entity or government sites or government program” but that offers no relief to the reader who wishes to stay informed but instead is presented with ads.
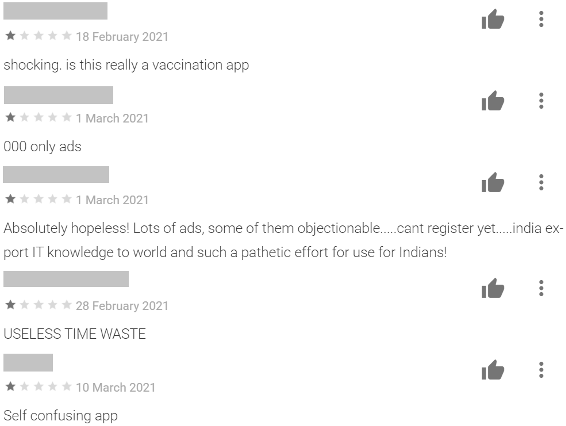
A quick look at the app shows us the ads the users are indicating:
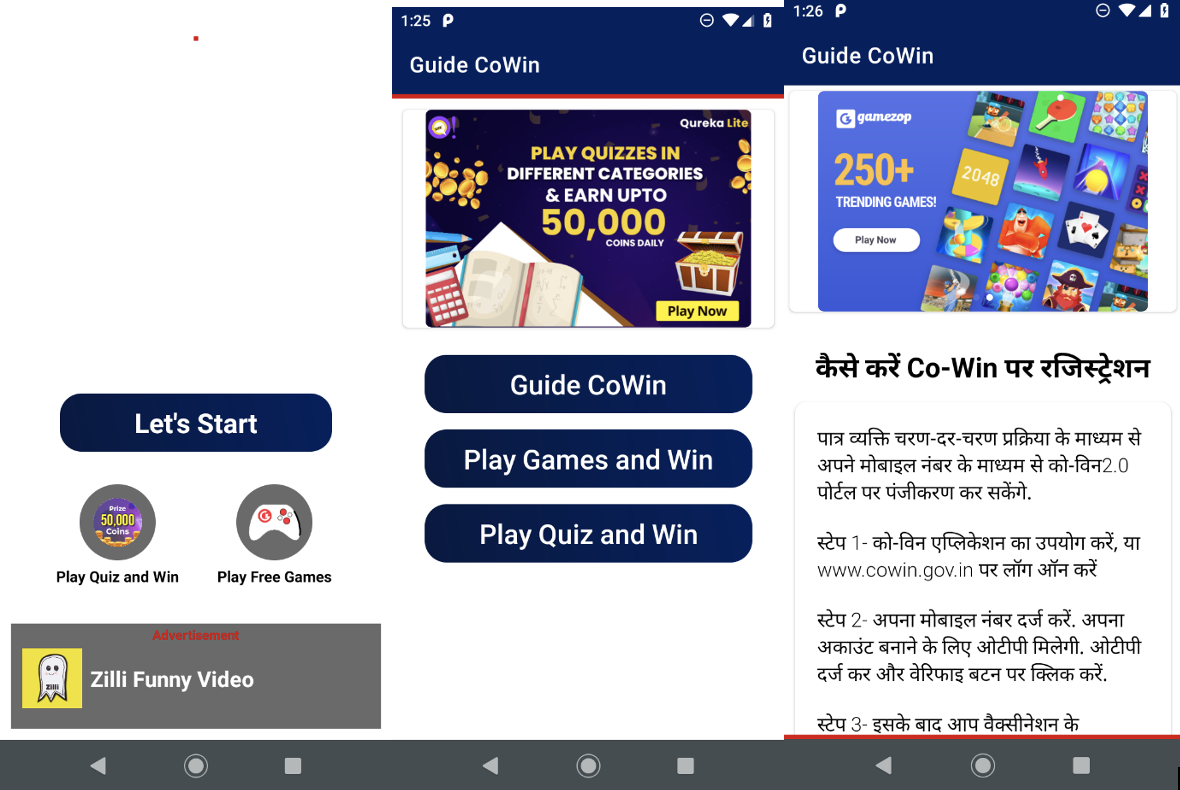
Google has been informed of this behavior; we advise users to avoid such applications until Google Play takes appropriate action.
We detect this threat as Android.Adware.Agent.BMF.
Conclusion
These examples are only the tip of the iceberg of vaccine-targeted apps. Malware and adware will continue to abuse people’s demand for vaccine. If there’s any lesson to be learned from this research, it’s that Android users should always be wary of apps requesting access to the Accessibility Service, as it’s the main access route for criminals into mobile devices.
We advise people to be vigilant and get any COVID-19 related information from known, proper channels and official government sources.
Indicators of Compromise
Hydra
Samples
| Md5 | Package name |
| af2e61a6778c3a3a1001f87ea9c96e80 | uniform.despair.grass |
| 56d07c9e9747c63ad8ee03a46fc5d26d | ball.ridge.fly |
Hydra targeted applications
| Package name | Application name |
| cl.android | Banco Falabella | CMR |
| co.com.bbva.mb | BBVA Colombia |
| com.bancocajasocial.geolocation | Banco Caja Social Móvil |
| com.bankia.wallet | Bankia Wallet |
| com.bankinter.launcher | BankinterMóvil |
| com.bbva.bbvacontigo | BBVA Spain | Mobile Banking |
| com.bbva.netcash | BBVA Net Cash | ES & PT |
| com.cajaingenieros.android.bancamovil | Caja de Ingenieros Banca MÓVIL |
| com.citibanamex.banamexmobile | CitibanamexMóvil |
| com.grupoavalav1.bancamovil | AV Villas App |
| com.indra.itecban.triodosbank.mobile.banki* | Triodos Bank. Banca Móvil |
| com.kutxabank.android | Kutxabank |
| com.mediolanum | Banco Mediolanum España |
| com.rsi | ruralvía |
| com.rsi.Colonya | ColonyaCaixaPollença |
| com.targoes_prod.bad | TARGOBANK – Banca a distancia |
| com.todo1.davivienda.mobileapp | DaviviendaMóvil |
| com.todo1.mobile | Bancolombia App Personas |
| es.bancosantander.apps | Santander |
| es.caixagalicia.activamovil | ABANCA- Banca Móvil |
| es.caixaontinyent.caixaontinyentapp | CaixaOntinyent |
| es.cecabank.ealia2103appstore | UniPayUnicaja |
| es.cm.android | Bankia |
| es.lacaixa.mobile.android.newwapicon | CaixaBankNow |
| es.liberbank.cajasturapp | Banca Digital Liberbank |
| es.openbank.mobile | Openbank – bancamóvil |
| es.univia.unicajamovil | UnicajaMovil |
| eu.netinfo.colpatria.system | Scotiabank Colpatria |
| net.veritran.becl.prod | BancoEstado |
| www.ingdirect.nativeframe | ING España. Banca Móvil |
*presumably meant to be com.indra.itecban.triodosbank.mobile.banking
Domains
| Domain/IP |
| Shabukenkeinside[.]com |
| Miinsaludgovcovacunacovid[.]com |
| miinsalud-gov-cl-vacuna-cvid19[.]com |
Cerberus
Samples
| MD5 | Package name |
| 0da756d28cead23b2c0e09573b2467ee | com.aivjutzyceew.jgiriaeg |
| 53550f69f2eecd26910fead5748e094b | com.lgiueovx.xlfhh |
Domains
| Domain/IP |
| 193.37.212.151 |
| Mohabmnho[.]surf |
Repackaged Adware
Samples
| MD5 |
| 93d7b7ba67c51d60a616fad011da0110 |
Co-Win Adware
Samples
| MD5 |
| 445095576fcd2ba8e9b67f48d19626fa |
| 88808208fe2a9d15a3a06782050c1f7a |
| ff47e1aa47f82701bbdf4808d26c7b09 |
| 5e90955d01a36a6eab26ac255b6a7fba |
| 5599679283cbc14ac7224dde5e3ef955 |
Bitdefender Mobile Security and Antivirus detects and removes all malware associated with this attack.