
COVID-19 has been a recurrent theme in phishing campaigns and cyberattacks this year, but threat actors haven’t exhausted the subject quite yet. While holiday-themed threat activity is still rampant during the shopping season, the discovery of the Omicron COVID-19 variant has opened new opportunities for criminals to expand their phishing repertoire.
Bitdefender Antispam researchers monitoring Omicron-related spam traffic have caught a malicious phishing campaign trying to infect recipients with a well-known data stealer.
The generic message is similar to a previous malspam campaign (serving the same malicious payload) and resembles a request to revise shipment information found in a Proforma invoice attachment. As expected, the attackers cite new government policies in response to the Omicron variant and offer no other information to recipients. Sample analysis has not shown any tailor-made versions targeting a specific organization or business.
“Please find attached PI. Still pending for confirmation of vessel. Kindly note that Government has some new policy in response to the OMICRON COVID-19 strain outbreak. Documents will be sent following final confirmation,” the email reads.
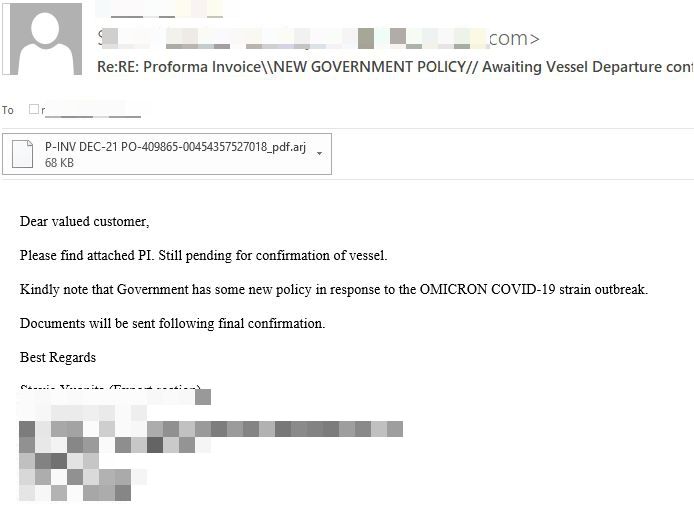
The attachment (P-INV DeC-21 PO-409865-00454357527018_pdf.arj) contains GuLoader, a remote access Trojan (RAT) downloader best known for its anti-VM capabilities to evade detection. The use of this downloader to spread malicious payloads such as FormBook, AgentTesla and Netwire has grown in popularity since its discovery in late 2019.
In this attack, cybercriminals use GuLoader to spread FormBook, a popular info-stealer spotted by Bitdefender researchers in global phishing campaigns in July and September 2021.
Attackers are impersonating an Indonesia-based company that makes packaging products to spread the form grabber malware. Over 90% of the malicious emails originate from IP addresses in the US and telemetry shows a clear focus on Asia-based targets. However, the campaign has spread globally, popping up in inboxes across Europe including the UK, Germany and the Netherlands.
Formbook is notorious for harvesting login credentials and banking-related data on web forms. While our researchers couldn’t attribute the campaign to any specific group, the attackers are motivated by money.
We expect more threat actors to piggyback on Omicron in coming weeks, as users travel or prepare for Christmas and New Years’ celebrations. Users are advised to stick to good cyber hygiene and install a security solution on their devices. Keep operating systems and apps up to date and never access attachments from unsolicited emails without being able to verify their validity.
Bitdefender customers are already protected from FormBook malware. The attached file, detected as Trojan.GenericKD.38151652, is blocked by both our consumer and enterprise solutions.
With Bitdefender Total Security and XEDR, users and businesses enjoy the best anti-malware protection and threat detection and response against e-threats across all major operating systems. The real-time protection feature included in our security software safeguards against e-threats, including viruses, worms, Trojans, ransomware, zero-day exploits and spyware, to keep you and your data safe.
Note: This article is based on technical information courtesy of Bitdefender Labs