
- Detailed exposé of a potential Chinese APT group targeting Southeast Asian governments
- Extensive custom toolset designed for reconnaissance, data exploration and exfiltration
- Sophisticated and distributed attack infrastructure remains partially operational to this day
- Bitdefender technology detects the malicious payloads and maps the behavior in each stage of the attack
Bitdefender threat researchers recently put the finishing touches on an investigation of a long-running, sophisticated APT attack campaign targeting government entities in Southeast Asia, an attack whose infrastructure likely continues to be active today. Attack artifacts shows signs of a Chinese APT group that we believe to be state sponsored. Geopolitical tensions in the region are always present, and information exfiltrated by an APT campaign can yield commercial and military advantages to various adversaries and could compromise government actors should embarrassing political or personal information be revealed.
Check out the Executive Summary
Targeted APTs once required government sponsors or direct financial motivation (e.g. intellectual property), however they are now commoditized to the point where the same tools can be used to attack any target of opportunity. The complete technical details of the investigation including the attack timeline, toolkit and TTPs employed are available in a detailed research report on Bitdefender Labs.
In this article, we’ll delve into how specific technologies in an endpoint security stack can detect sophisticated multi-stage attacks during each step in the attack kill chain and focus on how automatic EDR mapping of each detection element to the MITRE ATT&CK® Framework tactics and techniques can provide early warning signs of a potential breach while guiding swift and comprehensive remediation efforts by InfoSec teams.
Target Selection and Presumed Objectives
Target analysis indicates primarily Southeast Asian government institutions, although other targets are also probable. Our analysis of the campaign activity and tools used indicate a robust reconnaissance and data collection effort centered around sensitive document retrieval and exfiltration using distributed infrastructure.
Exploit Tools and Techniques
During the investigation, Bitdefender researchers also found that threat actors had an entire toolset in place, featuring powerful spying capabilities, backdoors and document collection mechanisms. The attackers achieved persistence on the target machines via digitally signed binaries that allow for the side-loading of backdoor tools into memory. Specifically, we identified three backdoors used for command and control (C&C): Chinoxy, PCShare and FunnyDream.
Execution Flow
The typical execution flow under this attack campaign is as follows:
- Execution of Chinoxy dropper and execution of the Chinoxy Backdoor
- Execution of PcShare dropper and execution of PcShare Loader
- Ccf32 deployment
- FilePakMonitor dropper deployment and FilePakMonitor execution
- FunnyDream backdoor deployment
- Deployment of other tools from the toolset: droppers of the FunnyDream tools, PcMain, FunnyDreamTcpBridge, FunnyDreamFilePak
Pictographically, the flow looks like this:
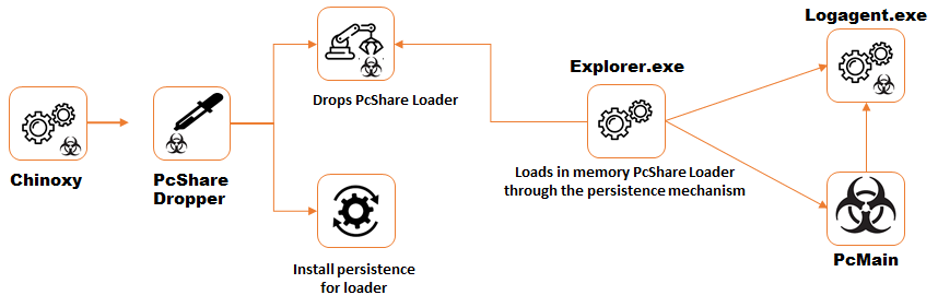
We also see clear evidence of an extensive custom toolset designed for data exploration and exfiltration and the use of spyware tools including Filepak for file collection, ScreenCap for taking screenshots and Keyrecord for logging keystrokes on the victims’ systems, all packaged up for delivery to systems controlled by the attackers.
Command and Control
Based on Bitdefender telemetry analysis, we have concluded that most of the C&C infrastructure for this APT campaign is located in Hong Kong, although we have also identified servers in Vietnam, China and South Korea. At least 7 different binary files contain hard-coded domains and IP addresses tied to attack infrastructure, two dozen of which we have uniquely identified in our research report. The distributed C&C infrastructure primarily controls the three backdoors. Having C&C infrastructure in the same region as the likely attack targets tends to draw less suspicion to the IP traffic that remote communications from outside the region. Additional evidence suggests threat actors may have compromised domain controllers within the victim’s network, allowing lateral movement and the potential to gain control over numerous machines within that victim’s infrastructure.
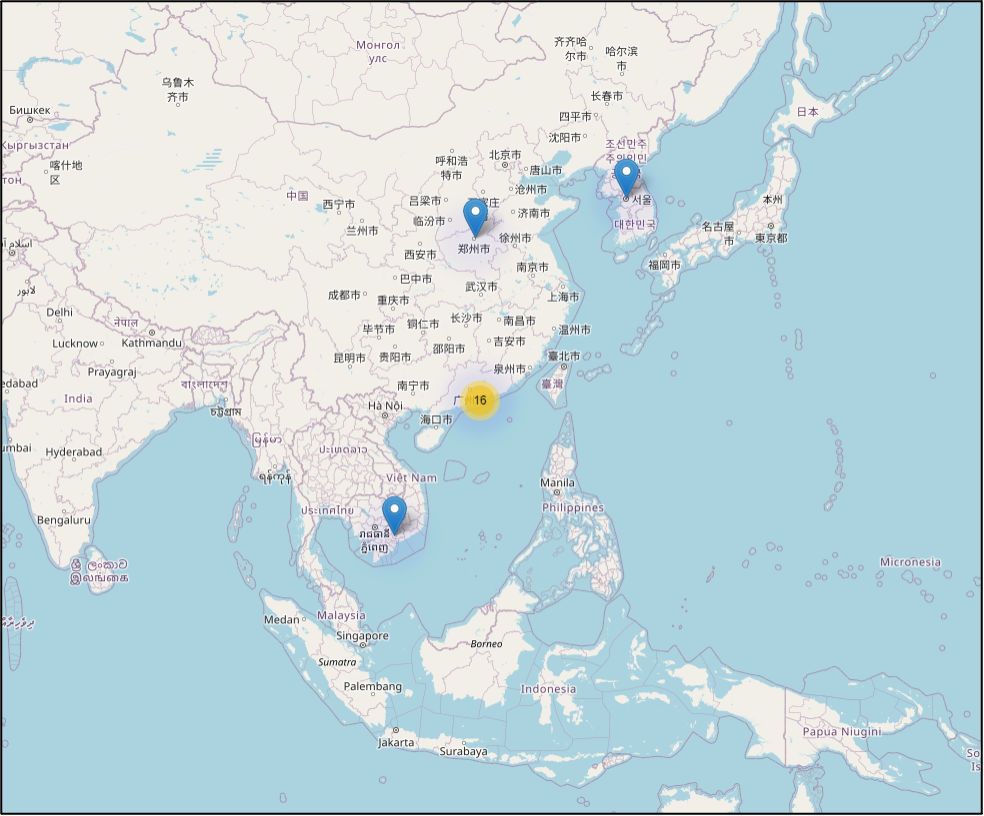
APT Campaign Reach
Analysis of this long-running campaign has revealed attack artifacts dating from late-2018 through 2020. Over 200 machines showed attack indicators associated with this APT campaign and the attack infrastructure likely continues to be at least partially active today.
Attack Attribution
Attributing APT style attacks to a particular group or country can be extremely difficult—as false-flag forensic artifacts can be manufactured, C&C infrastructure can reside anywhere in the world, and the tools used can be repurposed from other APT groups—however, evidence suggests a Chinese-speaking APT group using Chinese language binaries, and the Chinoxy backdoor used during the campaign is a Trojan known to have been used by Chinese-speaking threat actors.
MITRE ATT&CK™ Maps Tactics to Attack Stages
Nearly every organization at this point has implemented basic endpoint security technologies to protect against garden-variety malware and to facilitate compliance reporting, however more advanced threats are routinely designed to evade these traditional defenses and escape detection. The conventional security stack primarily involves file-based detection technologies, which can sometimes miss sophisticated attacks for reasons including polymorphic malware, fileless malware or the misuse of legitimate tools known as “living-off-the-land.”
MITRE has created a knowledge base of adversary tactics and techniques based on real-world observations that help organizations identify signs of potential breach that would otherwise be missed by the traditional security stack. While most security solutions focus on identifying malicious files or URLs, MITRE’s framework can be used to map specific techniques and tactics throughout the attack lifecycle, such as file and directory discovery, command line interfaces being triggered, remote management tool usage and automated scripting. While not malicious actions per se, these tactics techniques and procedures (TTP) can indicate suspicious activity associated with advanced threat actors performing various actions.
Bitdefender has aligned our products to the MITRE ATT&CK Framework as a common industry reference standard for detection efficacy and comprehensive understanding of end-to-end attack campaigns.
During our investigation into this APT attack campaign against various government entity targets, our EDR (Endpoint Detection and Response) technology flagged numerous MITRE attack techniques employed, mapped to essential stages of the attack chain:
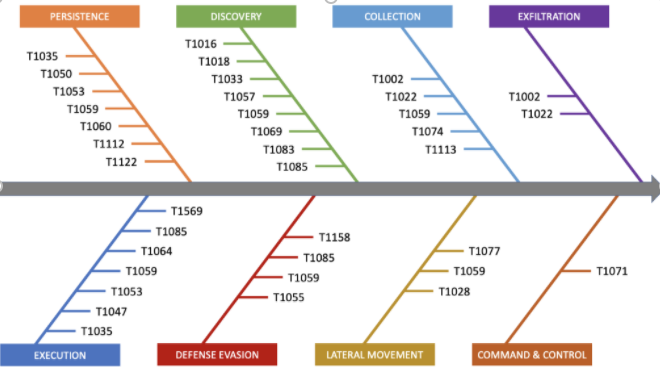
| MITRE ATT&CK Techniques Identified in the Campaign | |
| T1002 – Data Compressed | T1060 – Registry Run Keys / Start Folder |
| T1016 – System Network Configuration Discovery | T1064 – Scripting |
| T1018 – Remote System Discovery | T1069 – Permission Groups Discovery |
| T1022 – Data Encrypted | T1071 – Standard Application Layer Protocol |
| T1028 – Windows Remote Management | T1074 – Data Staged |
| T1033 – System Owner/User Discovery | T1077 – Windows Admin Shares |
| T1035 – Service Execution | T1083 – File and Directory Discovery |
| T1047 – Windows Management Instrumentation | T1085 – Rundll32 |
| T1050 – New Service | T1112 – Modify Registry |
| T1053 – Scheduled Task | T1113 – Screen Capture |
| T1055 – Process Injection | T1122 – Component Object Model Hijacking |
| T1057 – Process Discovery | T1158 – Hidden Files and Directories |
| T1059 – Command-Line Interface | T1569 – System Services |
MITRE ATT&CK® alerts can help organizations investigate signs of intrusion and address critical security blind spots like restricting access to unused ports, hidden command-line interfaces and remote access tools, allowing InfoSec teams to set policies restricting these tools from executing on endpoints without user knowledge.
Bitdefender Technology Stack Blocks Malicious Payloads and Maps Suspicious Behavior
MITRE ATT&CK is powerful in terms of mapping suspicious and malicious behavior to the relevant attack stage, but the security stack plays an essential role in both prevention and detection, as it blocks many aspects of the attack and lays out a roadmap for remediation of further detections in the hands of a skilled security analyst. For example, against the Bitdefender security stack, the investigated APT attack campaign is readily detected and blocked by multiple Bitdefender security technologies during various steps in the attack chain sequence.
Page Break
Bitdefender anti-malware technology successfully detects and
blocks numerous malicious APT campaign payloads throughout the kill chain, including the following examples:
- Gen:NN.ZexaN.40013.zu0@aSMEfCfi
- Gen:Variant.FunnyDreamBackdoor.Johnnie.3
- Gen:Variant.FunnyDreamDllDeploy.Johnnie.9
- Gen:Variant.FunnyDreamFilePakMonitor.Mikey.1
- Gen:Variant.Graftor.756437
- Gen:Variant.Ser.Zusy.2791
- Gen:Variant.Zusy.304040
- Trojan.Agent.EXBP
- Trojan.Agent.EXBQ
- Trojan.ChinoxyBackdoor.GenericKD.33909778
- Trojan.FunnyDreamFilePak.A
- Trojan.FunnyDreamTcpBridge.A
Process Inspector detects multiple components on execution using Advanced Threat Control, resulting in the detection: ATC.SuspiciousBehavior.
Additional detections are facilitated by Bitdefender prevention and detection technology layers:
- Bitdefender HyperDetect technology, which uses highly tuned machine learning models for spotting new and unknown malware with 99.99% accuracy
- Bitdefender Theta technology, which is 100% machine learning-powered and uses deep neural networks and state-of-the art cloud-based dynamic behavioral analysis
- Bitdefender URL-Status technology, used for identifying malicious, fraudulent or suspicious links, also blocks malware’s attempts to contact the Command & Control server, potentially plugging the attacker’s ability to remotely control the threat by giving it further instructions or blocking it from exfiltrating data
- Bitdefender ATC (Advanced Threat Control) and Sandbox are two dynamic detection technologies that detect threats, even when they are sandbox-aware and designed with evasive capabilities
- Bitdefender Network Attack Defense, a technology focused on detecting network attack techniques designed to gain access to endpoints
See the Bitdefender EDR Advantage
Fighting APTs Requires Prevention and Detection
A comprehensive endpoint security stack that identifies suspicious behavior and malicious payloads across different aspects of the attack chain (e.g., on download, on installation, on access, on execution) is essential to blocking various aspects of advanced attacks. However, it is necessary but not sufficient in that blocking threats often fails to reveal the full intent and scale of an attack, so an EDR solution that maps attack tactics and techniques to the MITRE ATT&CK Framework is the next step towards both understanding and blocking where the attack originated and how far in the attack chain attackers managed to reach.
Learn more about Bitdefender’s technology stack
ATPs evolve quickly while attack TTPs and toolsets spread readily among cybercriminals and other threat actors. APT “mercenaries for hire” repurpose attacks for any targets of opportunity, regardless of size or industry. As such, it is now more important than ever to turn to capable and easily manageable EDR solutions that can correlate suspicious events into comprehensive incidents that the security stack might otherwise dismiss.
For InfoSec teams short on time or lacking certain skill sets, Managed Detection and Response (MDR) solutions position a set of cross-functional cybersecurity experts to closely watch for anomalies and suspicious activity, conduct threat hunting missions and keep customers informed through attack containment and remediation.
Explore Bitdefender Managed Detection and Response
Bitdefender Partners, Resellers and Advanced Threat Intelligence Users
- Detections for this APT campaign are included in the Bitdefender Anti-Malware SDK for OEM Partners
- Threat Intelligence partners receive early warning of binaries and attacker TTPs used in this campaign
- Managed Services Providers benefit from these detections in Bitdefender Cloud Security for MSPs
Today’s targeted APTs quickly become tomorrow’s commodity attacks and remote campaigns rarely stay far away for long. Speak with a Bitdefender representative to discover the industry-leading products and services that are right for you to help keep your business protected against an ever-changing global threatscape.