
Europol and law enforcement agencies from 11 countries just dealt a heavy blow to FluBot, shutting down its infrastructure and essentially rendering the malware inactive.
FluBot made a name for itself over the past few months, especially in Europe and Australia, as it aggressively spread through SMS messages. One reason for its “success” was its use of infected devices to spread to other Android devices, mirroring the infection path of a biological virus.
Because the threat was widespread across multiple continents, it required the cooperation of numerous countries, including Australia, Belgium, Finland, Hungary, Ireland, Spain, Sweden, Switzerland, the Netherlands and the US, with Europol’s European Cybercrime Centre (EC3) coordinating international activity.
FluBot grew exponentially
While the name FluBot might not inspire fear, the threat is actually insidious. Potential victims receive an SMS accompanied by a message that tries to persuade them to install an app.
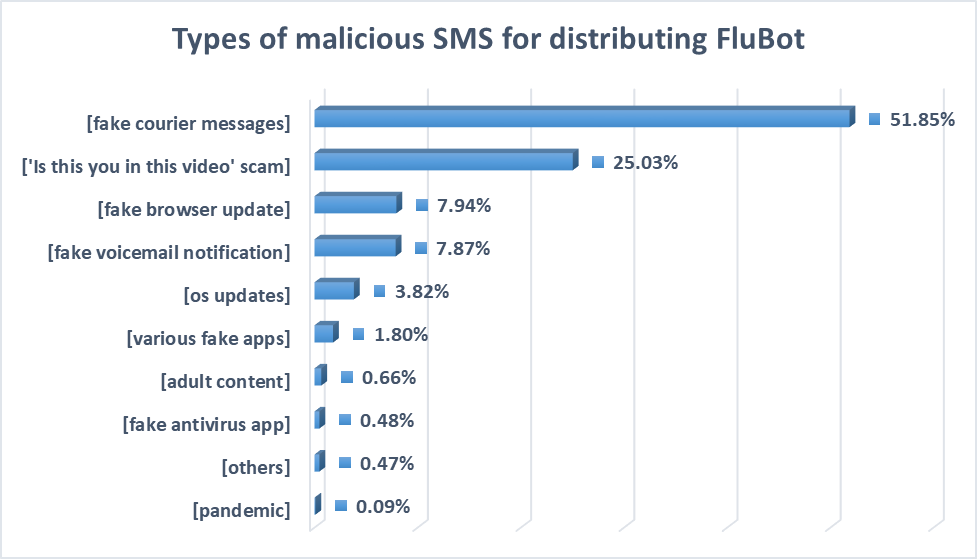
The application is actually a banker trojan that immediately grabs contact lists and uses the Accessibility services to monitor e-banking apps and cryptocurrency account details.
While the criminals designed the malware for the Android platform, our research showed that its operators accounted for SMS messaging arriving on iOS devices. In that situation, accessing the link redirects to a phishing website so that the attackers could still profit in the absence of an infected device.
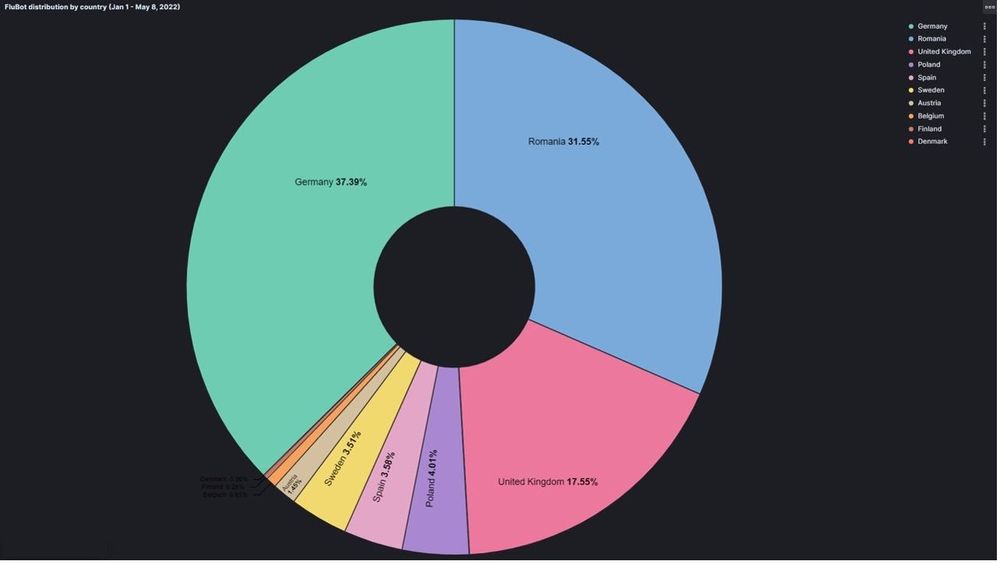
The last waves FluBot made in Europe were quite significant, with the malware targeting Germany, Romania, UK, Poland, Spain, Sweden, Austria, Finland and Denmark. Interestingly enough, our research also revealed that the attackers didn’t focus on all countries at once. They targeted a few countries for a few days, quickly switching to another group of states a few days later, likely to stay ahead of law enforcement.
Taking down the infrastructure
FluBot appeared at the end of 2020, but started to gain significant traction in the following months. Bitdefender identified a global campaign in June 2021, followed by numerous waves that increased in severity.
Europol revealed few details of their investigation and didn’t say if they actually arrested anyone during their operation. However, they said the entire FluBot infrastructure is now under the control of law enforcement, allowing them to stop the spread.
All the information stolen from Android devices, including Contacts, was sent to servers that controlled the entire operation. Most likely, law enforcement seized the communication infrastructure, which means that infected devices can’t send back the information and won’t receive the proper commands to send SMS messages to other people.
At least for the time being, the flow of SMS messages carrying links to the Flubot malware should slow down, if not completely stop. Users should remain wary of messages from unknown numbers and of clicking on links. A security solution such as Bitdefender Mobile Security for Android that can identify all threats, including the ones circulating through SMS, is recommended.