
Dutch police have arrested suspected members of a notorious cybercrime gang known as “Fraud Family,” following a spate of sophisticated phishing attacks that have targeted users in the Netherlands and Belgium.
A 24-year-old man from Arnhem, suspected of developing and distributing phishing frameworks that collected data from unsuspecting banking customers, was arrested on Tuesday and was scheduled to be brought before a magistrate in Rotterdam today.
Also arrested was a 15-year-old boy from the town of Loenen aan de Vecht, suspected of selling the phishing panels which could have made it easy for criminals with minimal technical knowledge to launch convincing phishing attacks and even bypass two-factor authentication (2FA.)
Security experts at Group IB believes that the people arrested are part of a “Fraud-as-a-service” criminal ring known as “Fraud Family.”
As researchers describe in a blog post, Fraud Family have created an infrastructure involving phishing kits and web admin panels that allow criminals to interact in real-time with a phishing website.
For instance, a victim might be sent a message via email, SMS, or WhatsApp which includes a link to a phishing website. The message may claim to be a notification from an online marketplace, a bank, or other service that requires attention from the unsuspecting user.
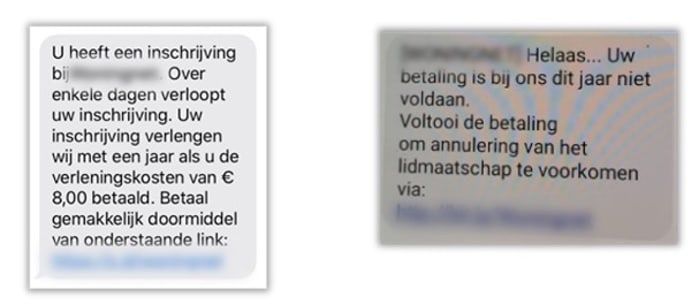
If clicked, the links take the user to a phishing page which looks virtually identical to a legitimate banking website, with a request for the user to login – providing their personal and banking information.
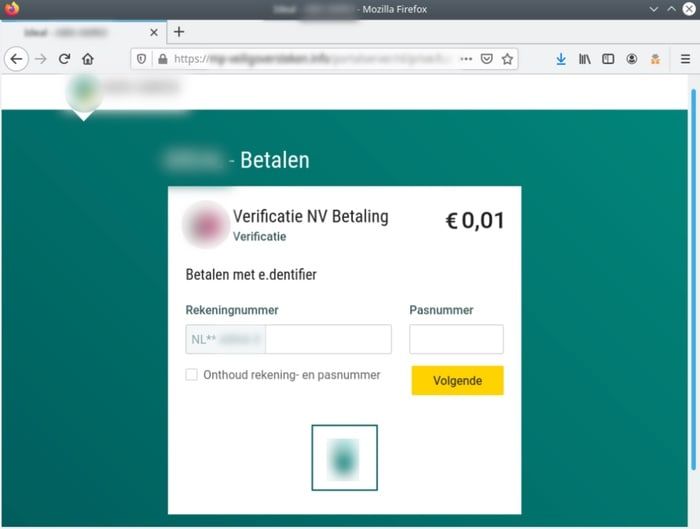
Of course, most banking users have their accounts protected by more than just a simple username and password today – such is the prevalence of phishing scams – and so the fraudsters are able to interact with the user in real-time via an admin panel, stealing information and credentials throughout.
As Group IB describes, as victims enter their credentials on a phishing site the fraudsters are informed of the activity:
“The crooks who use this phishing infrastructure get access to a web panel that interacts, in real time, with the phishing site. When victims submit their banking credentials, the phishing site sends them to the fraudster-controlled web panel. This one actually notifies the miscreants that a new victim is online. The scammers can then request additional information that will help them to gain access to the bank accounts, including two factor authentication tokens, and personal identifiable information. While the phishing site is waiting for further instructions from the attackers, the unsuspecting victim is looking at a “Please wait…” screen.”
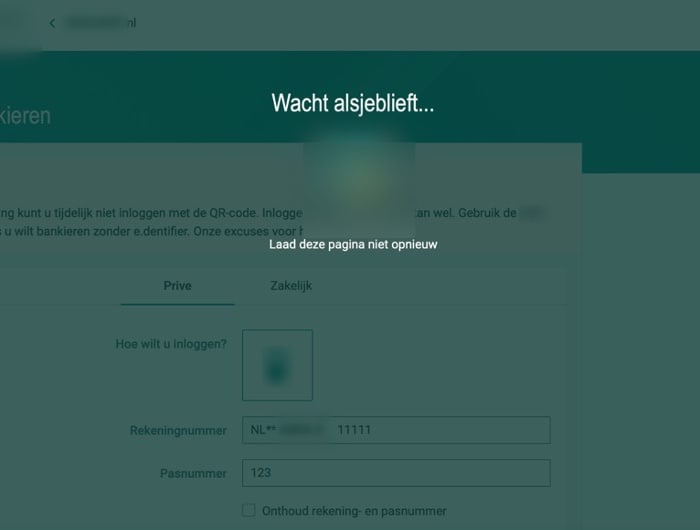
In short, a fraudster can use information given to them by the victim to attempt to break into a banking account, and additionally request in real-time any further information that the bank requires to complete the login process – such as a 2FA code or even engage in a live online chat posing as customer support.
Promoting itself on Telegram, Family Fraud has been renting out its services to criminals for as little as €200 a month. Thousands of subscribers have joined the Telegram channels operated by the group, suggesting large sums may have been made from the criminal activity.
Fascinatingly, even the Dutch police have appeared in the group’s Telegram channel – publicising the arrest of suspected gang members.
According to police, a firearm, telephones, and computers were seized in the searches at the suspects’ properties. In addition the source code of the phishing panel is said to have been found.
Internet users are advised to remain extremely wary of unsolicited links that they are sent, and only enter information on webpages which they are confident are legitimate.