
* IoT camera’s admin passwords were easy for local attackers to determine * Once vulnerabilities had been exploited, unauthorised users could easily watch a live feed from compromised devices. Anyone buying a home security camera is probably buying it with the intention of increasing their security, not decreasing it.
And yet once again an internet-enabled CCTV camera has proven itself to be vulnerable to attack, allowing Peeping Toms to spy on unsuspecting users who believe they are safe in the privacy of their home.
Experts at Bitdefender publicly announced this month that they had found serious vulnerabilities in LifeShield home security cameras that could have allowed hackers to live-stream your home without your permission.
Upon closely examining the LifeShield home security camera (now known as Blue by ADT), Bitdefender’s researchers found that security weaknesses made it possible for a local attacker to:
- Obtain the security camera’s administrator password, simply by knowing a camera’s MAC address.
- Inject commands to gain root access to the device.
- Gain unrestricted access to the camera’s audio and video feed.
In a technical white paper produced by Bitdefender, researchers explained how they were able to trick Lifeshield cameras into spilling their administrator passwords:
“The doorbell periodically sends heartbeat messages to cms.lifeshield.com containing information such as the MAC address, SSID, local IP address and the wireless signal strength. After receiving such a message, the server tries to authenticate to the camera using the basic authentication scheme. This means the password for the administrator can be obtained by decoding the base64 authorization header received in this request.”
“The server seems to ignore the token and checks only the MAC address when sending a response, which allows an attacker to craft a fake request and obtain the credentials for any device.”
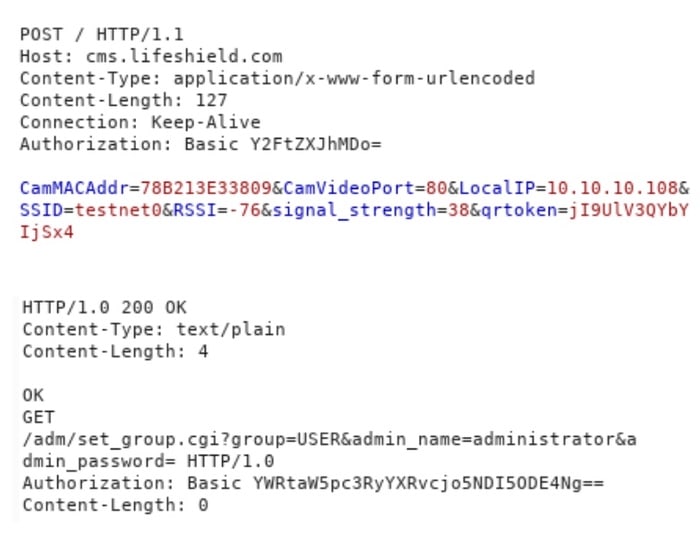
Once credentials have been stolen it is trivial for an unauthorised attacker to access the camera’s web interface and access its functionality.
The researchers noted that attacks would be particularly effective in situations where hackers would be within close range to the same wireless network, such as multi-tenant environments, and shared homes.
Bitdefender’s experts first attempted to resolve the issue by contacting the vendor at the beginning of February 2020. Unfortunately no response was received to this, and subsequent attempts to reach out, until the end of June 2020 – almost five full months later.
ADT pushed out an automatic update for vulnerable devices in mid-August 2020, and technical details of the security holes are only being published now because it is felt enough time has passed for most users to have benefited from the protection.
As ever, consumers would be wise to do their research before buying internet-enabled products, determining which vendors have a track record of reliably pushing out security updates to their products when vulnerabilities are found. In addition, it’s always a good idea to change default passwords and put different IoT devices on separate subnetworks.