
Hundreds of millions of people around the world use dating apps in their attempt to find that special someone, but they would be shocked to hear just how easy one security researcher found it to pinpoint a user’s precise location with Bumble.
Robert Heaton, whose day job is to be a software engineer at payments processing firm Stripe, discovered a serious vulnerability in the popular Bumble dating app that could allow users to determine another’s whereabouts with petrifying accuracy.
Like other dating apps, Bumble displays the approximate geographic distance between a user and their matches.

You might not think that knowing your distance from someone could reveal their whereabouts, but then maybe you don’t know about trilateration.
Trilateration is a method of determining an exact location, by measuring a target’s distance from three different points. If someone knew your precise distance from three locations, they could simply draw a circles from those points using that distance as a radius – and where the circles intersected is where they would find you.
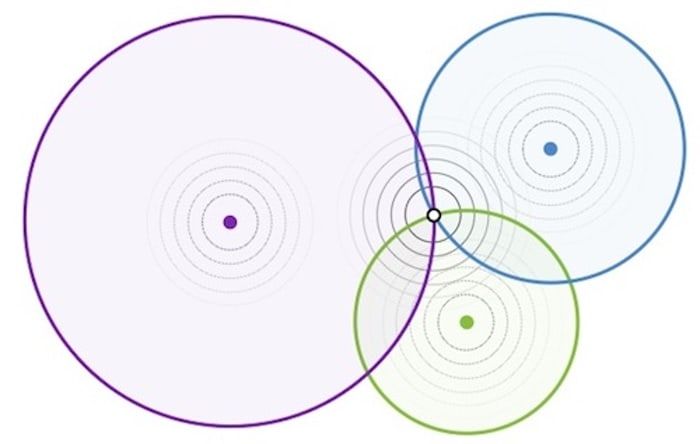
All a stalker would have to do is create three fake profiles, position them at different locations, and see how distant they were from their intended target – right?
Well, yes. But Bumble clearly recognised this risk, and so only displayed approximate distances between matched users (2 miles, for instance, rather than 2.12345 miles.)
What Heaton discovered, however, was a method by which he could still get Bumble to cough up enough information to reveal one user’s precise distance from another.
Using an automated script, Heaton was able to make multiple requests to Bumble’s servers, that repeatedly relocated the location of a fake profile under his control, before asking for its distance from the intended victim.
Heaton explained that by noting when the approximate distance returned by Bumble’s servers changed it was possible to infer a precise distance:
“If an attacker (i.e. us) can find the point at which the reported distance to a user flips from, say, 3 miles to 4 miles, the attacker can infer that this is the point at which their victim is exactly 3.5 miles away from them.”
“3.49999 miles rounds down to 3 miles, 3.50000 rounds up to 4. The attacker can find these flipping points by spoofing a location request that puts them in roughly the vicinity of their victim, then slowly shuffling their position in a constant direction, at each point asking Bumble how far away their victim is. When the reported distance changes from (say) 3 to 4 miles, they’ve found a flipping point. If the attacker can find 3 different flipping points then they’ve once again got 3 exact distances to their victim and can perform precise trilateration.”
In his tests, Heaton found that Bumble was actually “rounding down” or “flooring” its distances which meant that a distance of, for instance, 3.99999 miles would actually be displayed as approximately 3 miles rather than 4 – but that didn’t stop his methodology from successfully determining a user’s location after a minor edit to his script.
Heaton reported the vulnerability responsibly, and was rewarded with a $2000 bug bounty for his efforts. Bumble is said to have fixed the flaw within 72 hours, as well as another issue Heaton uncovered which allowed Heaton to access information about dating profiles that should have only been accessible after paying a $1.99 fee.
Heaton advises that dating apps would be wise to round users’ locations to the nearest 0.1 degree or so of longitude and latitude before calculating the distance between them, or even only ever record a user’s approximate location in the first place.
As he explains, “You can’t accidentally expose information that you don’t collect.”
Of course, there might be commercial reasons why dating apps want to know your precise location – but that’s probably a topic for another article.
Stay safe folks.