
The severity of a data breach typically jumps in the short term and decreases as time progresses. But, according to a survey by International Information System Security Certification Consortium, or (ISC)², the 2020 SolarWinds incident bucked that trend in the eyes of cybersecurity professionals.
Four months in, the infosec community is more concerned than ever about the infamous supply chain attack that resulted in the breach of more than 18,000 (confirmed) organizations. The reason? More details keep bubbling up as forensic investigations continue.
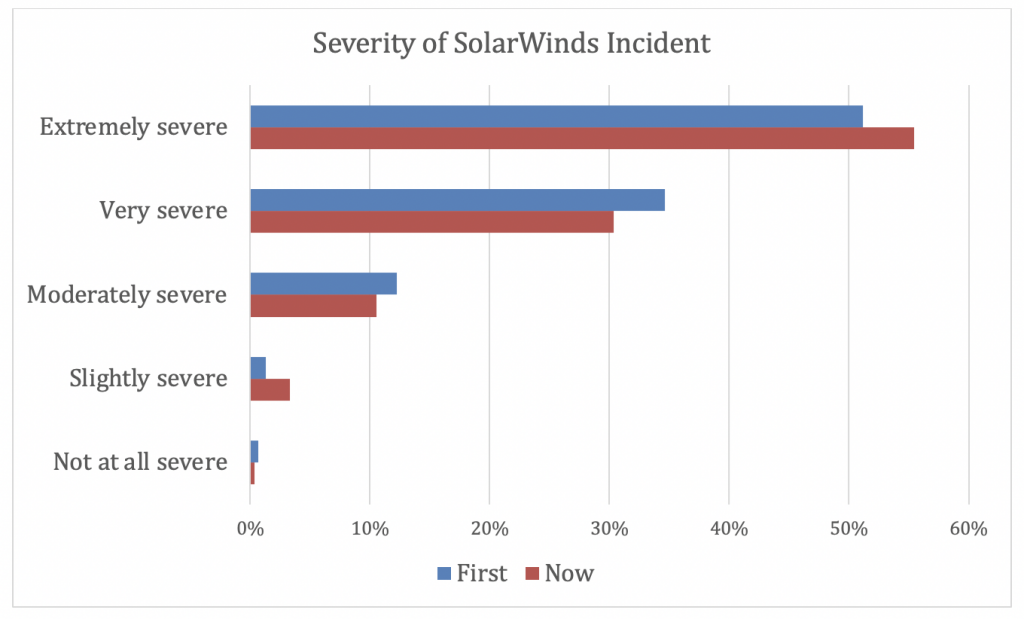
In a survey of 303 cybersecurity professionals fielded from February 10-28, 2021, 86% of respondents said they would have rated the breach ‘very’ or ‘extremely’ severe when they first learned about it, the (ISC)² reports.
However, a month and a half after the incident was reported, the number of respondents who indicated the breach was “severe” increased from 51% to 55%. On a scale from 1 to 5, the perception of the severity of the breach also increased over time, from an average of 4.34 initially up to 4.37.
“This perception of increasing severity is atypical of most breaches,” according to the consortium. “Headlines tend to fuel speculation in the immediate aftermath of a public disclosure, which is then tempered by remediation of the threat. In other words, severity spikes in the short term and decreases as more information becomes available.”
The incident has prompted reviews of security tools and protocols by many cybersecurity teams, (ISC)² analysts learned during the survey period. Decision makers reportedly stepped up activities such as forensic analyses, re-architecting of systems, and making sure all patches are up to date, in the wake of the incident.
Many fielded questions from their executive teams about their own security protocols, prompting time-consuming due diligence and reporting activities. And some had a lot of explaining to do, despite not being impacted by the breach, because they used a SolarWinds product.
“As a SolarWinds MSP customer, I have had to do a lot of explaining to our customers about what was involved in the breach and why we are continuing to use a SolarWinds product,” one respondent said.
Last but not least, the (ISC)² report includes a list of popular recommendations from those surveyed, including:
- Improve third-party governance and due diligence practices
- Improve controls to perform extra due diligence on any third-party software (say through automated software analysis)
- Watch outbound traffic and know what it should be
- Isolate systems with broad access to other systems
- Harden systems and conduct thorough research before deploying a solution
- Segment networks
- Employ a multi-faceted approach, incorporating humans and technology
- Improve IOC detection mechanisms
- Disallow internet access to systems that do not require it
As one respondent put it, “The principles are known: least privilege, cyber hygiene on credentials and software development best practices. This attack is a call for action to implement (these controls) at all levels.”