
- Simulated phishing campaign reveals recipients typically open the email 50% of the time, 32% click the malicious attachment or link, and 13% submit sensitive data
- Employees in Quality Management & Health, Purchasing / Administrative Affairs, Legal / Internal Control, Human Resources, and Research & Development have the highest rates opening and interacting with malicious emails
- Phishing attacks are winning because they target fundamental and typical human nature, researchers say
Users that deal with extensive email exchanges daily are proportionally more prone to phishing attacks than those that don’t. Hardly a surprise. But, according to one report, researchers have been able to pinpoint the exact industries and departments most prone to falling victim to email-borne cyber threats.
Data aggregated by Keepnet Labs from simulated phishing emails sent to over 410,000 target users reveals that recipients opened the email 50% of the time.
The report’s authors fail to explain what exactly they mean by “opening” an email. Supposedly they are referring to the action of clicking any unread item in their inbox.
More worryingly, 32% of users actually went on to click the malicious attachment or link, and around 13% submitted their information and thus enabled the attack to succeed.

The numbers are on par with a similar study the year prior, researchers say, so not much has changed in the phishing landscape since. But the report also underscores the business sectors and departments most likely to carry out these dangerous actions.
Department-based statistics collected from phishing tests show that employees in Quality Management & Health, Purchasing / Administrative Affairs, Legal / Internal Control, Human Resources, and Research & Development have the highest rates of not only opening malicious emails but also interacting with the malicious content and even submitting sensitive data back to the attacker. Unbeknownst to them, they are helping a malicious actor penetrate their employer’s infrastructure (see below graph, courtesy of Keepnet Labs).
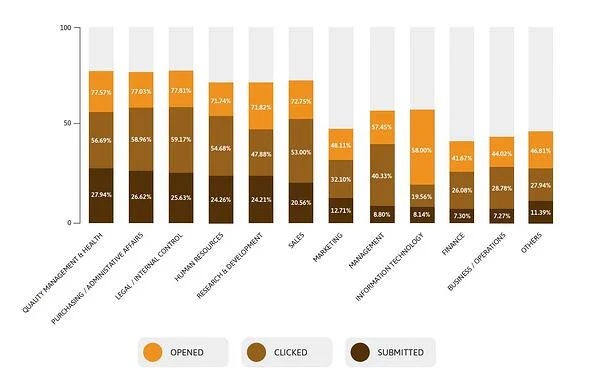
On the bright side, business departments like Finance and Business Units/Operations remain the most unlikely to read or open a phishing email, as in the previous years’ statistics, researchers said. In terms of clicking rate, Information Technology, Finance, and Business Units/Operations are the most resilient against phishing attacks, as in the previous year.
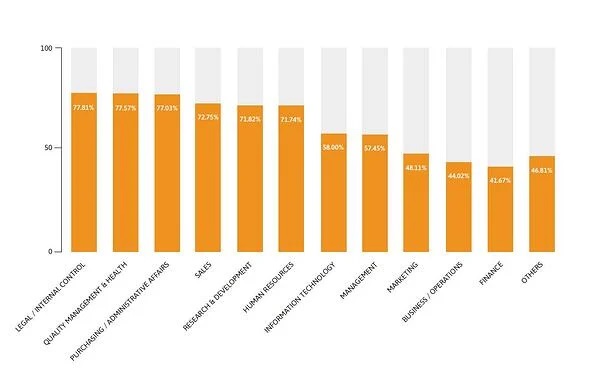
Researchers found that the top vulnerable departments (Legal/Audit/Internal Control, Purchasing/Administrative, and Quality Management/Health) have not changed since the previous year.
“It is essential to bear in mind that most of the sensitive information that cyber criminals require is accessible to users who operate in these units,” the authors noted. “This circumstance generates a serious threat to organisations because these specific individuals are keys to a doorway that lets hackers inside.”
In terms of sharing information with the attacker, employees in Quality Management/Health, Purchasing/Administrative, and Legal/Audit/Internal Control fare the worst, again just like the year prior.
“These statistics prove that specific departments are more inclined to share sensitive information. These departments need to pay more attention due to their positions,” researchers cautioned.
As far as industries go, businesses of varying sizes across more than 20 different sectors exhibit visible differences in cyber-awareness and resilience. For example, sectors like Consulting, Banking, Telecoms, and Transportation have high chances of falling victim to phishing scams. Consulting fares the worst, with 83% chances of opening a malicious email, 63% chances of interacting with the content inside, and 30% chances of submitting sensitive data to the attacker.
“Phishing attacks are winning because they target fundamental and typical human nature,” researchers said.
“Once these departments are jeopardised, it can have a devastating effect on any organisation. Besides the direct economic cost, such as theft of corporate information, breaches can lead to disruption to brand and reputation. There will also be legal and regulatory challenges to deal with in the aftermath of an incident,” they concluded.
Security solutions that embody human risk analytics enable IT administrators to act with surgical precision, increase security controls when and where they are needed, and even conduct training for staff members that need to get a better grasp on corporate security.