In recent years, no framework has become more prevalent than MITRE ATT&CK™, – the acronym standing for Adversarial Tactics, Techniques, and Common Knowledge. Why? Because it’s one of the most complete, complex and realistic cybersecurity models – and it’s constantly improving.
The MITRE ATT&CK framework
Based on a layered matrix that covers all possible attack vectors, this framework focuses on indicators of compromise and threat actor behavior, rather than singular threats. It enables the study of behavioral anomalies and maps them to real-world applicability, while constantly adapting to new methods.
Since its launch in 2015, the framework has been widely adopted by security providers, as it aids both offensive (red) and defensive (blue) security teams. As of April 2021, the enterprise version of the ATT&CK matrix contains 14 different tactics, 185 techniques, and 367 sub-techniques. A matrix for mobile environments exists, as well as one dedicated to industrial control systems.
The tactics themselves are broad categories based on attack vectors and their behavior. They answer the questions “What is the purpose of the attack?” and “What phase is the attack in?”
Applying the ATT&CK framework, cyber-threats are identified in the reconnaissance, resource development or initial access phase. Others can be identified during their execution or persistence phase. Privilege escalation, defensive evasion and credential access are also analyzed, as well as discovery and lateral movement techniques. The framework also checks for data collection, command & control, and exfiltration behavior, and reserves its last category for threat impact.
Each phase comes with its own techniques, and a threat can shift through multiple tactics at once. For example, a threat that’s trying to evade defenses by hijacking an execution flow (the way an OS runs its programs), might also try to escalate privileges with a similar technique. In fact, APTs are often in multiple phases and use a wide range of tactics to reach their goals.
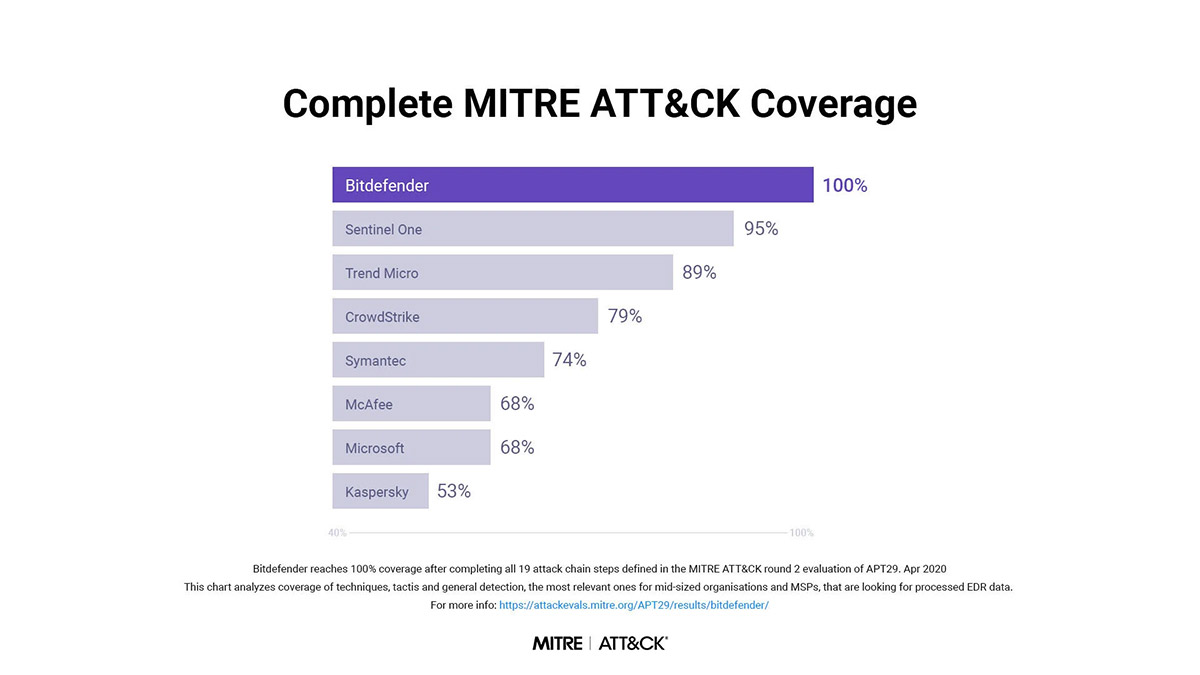
Bitdefender and MITRE ATT&CK
Last year saw the highly anticipated release of the MITRE ATT&CK Evaluation framework. Unique to independent testing, this evaluation simulates a sophisticated attack, while also requiring the disablement of any blocking feature a security solution might have. In other words, it forces a security platform to rely on experience, efficiency and intelligence, rather than simple evasion.
Bitdefender achieved the highest number of detections across all attack steps and sub-steps (366), providing extended visibility and context. This made Bitdefender’s, with a nearly 50% greater average of detections than the other 29 participating vendors.
Not only did Bitdefender provide analytics insights for 96% of all detections, it also spotted 100% of attack techniques against Linux systems – an important achievement, considering many enterprises run Linux servers in their operations.
What does this mean for your security team?
Bitdefender solutions not only provide the widest coverage, but also save the most resources and prevent alert fatigue – ensuring minimal false positives occur. By covering all steps of the attack chain, Bitdefender offers the highest chances of spotting complex attacks before catastrophic damage occurs.
MITRE ATT&CK is not a theoretical framework, but one that’s meant to be used daily. Aside from offering a common starting point for security analysts, the framework offers a chance to map your defensive controls, perform threat hunting and digital forensics, and map your vulnerabilities to attack techniques. This way, you’re protected against known malware and future threats.
The latest evaluation validates Bitdefender’s unique combination of EDR, network security, analytics and threat intelligence as an optimal choice for enterprises and managed security services providers (MSSPs) looking to improve cyber resiliency.
Learn more about how MITRE ATT&CK Evaluation testing results can reduce cybersecurity operational costs.