
It would be almost impossible to use a computer or network for business and be unaware of ransomware. But what about ransomware families?
If you manage cybersecurity or own a small to medium-sized business, it’s becoming increasingly important to be more than just aware of ransomware. You need to have a grasp of how the ransomware used in a predominant number of cyberattacks cripples a business’s systems and commandeers its data.
Ransomware attacks in the United States increased by 300% in a year, and small businesses accounted for 50% or more of the incidents, says Homeland Security Department Secretary Alejandro Mayorkas, who shared that data at a U.S. Chamber of Commerce event in spring 2021.
Despite intensified private and public efforts to identify and arrest cyberthieves and thwart ransomware attacks, the evolution of ransomware as a service (RaaS) — where bad actors provide access to the victim’s network to a RaaS group, which collects the ransom payment and splits it with the bad actors — means it’s unlikely that the threat will diminish anytime soon.
The rise of RaaS and ransomware families
What do “families” have to do with cyberattacks?
“Families are directly related to the modern RaaS model,” explains Martin Zugec, technical solutions director at Bitdefender. “Ransomware infection is just the final step; these modern attacks take some time to prepare and threat actors will try to thoroughly prepare before launching an attack.”
The bulk of cyberattacks tend to be built on less than two dozen ransomware families. Ransomware families are the common code signatures, the viral payloads, and malicious commands that do the dirty work once they gain access to a business’s systems. They also share a similar attack style and know-how — a sort of playbook — for affiliates.
Typically, RaaS leads the ransom negotiations so researchers often rely on the ransom note to identify the family (and respond to an ongoing attack accordingly). You can find out more how Bitdefender was able to identify REvil attacks from its ransom letters here.
In all, cybersecurity experts suspect that there are roughly 250 known ransomware families.
Trying to deploy security tools to thwart hundreds of types of any cyberthreat sounds daunting. But because ransomware is just the final step in a modern attack, detection and response becomes ever so important.
Learning how the most prolific families operate and implementing security tools trained to spot familial signature codes can help your business and security team better defend against ransomware. It also will also help you identify and shore up the vulnerabilities and threat vectors that make your business susceptible to ransomware.
What are the most notable ransomware families?
In a September analysis of 12.7 million malware detections, Bitdefender identified 220 ransomware families.
The number of ransomware families detected varies each month, depending on current ransomware campaigns worldwide. That said, just three families — WannaCryptor, Stop/DJVU, and Phobos — accounted for 59% of the attacks associated with the top 10 ransomware families in September’s analysis.
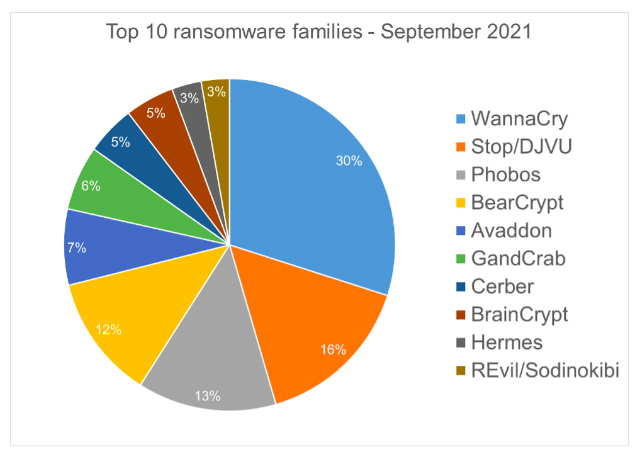
SOURCE: Bitdefender Threat Debrief | September 2021
The uptick in ransomware incidents the past few years, particularly as a tool of cybercrime syndicates and cyberthieves loosely affiliated with specific ransomware families, has pushed these attacks to among the main cyberthreats worldwide.
Here’s why: Ransomware is big business for digital criminals.
Consider the recent arrests and charges of affiliates of the REvil/Sodinokibi ransomware family that took part in the Kaseya Software attacks this summer. The U.S. Justice Department recovered $6.1 million from just one man’s account, the money that was extorted from ransomware victims.
Quick anatomy of a ransomware attack
Ransomware is not a new phenomenon. The first ransomware attack dates to 1989, with the AIDS Trojan/PC Cyborg that targeted healthcare organizations.
Modern ransomware typically falls into two categories: crypto and locker.
- Crypto ransomware encrypts a business’s files so that it can no longer access them.
- Locker ransomware behaves just as you might expect and locks a business out of some or all of its systems and files entirely.
In both instances, attackers prevent access to resources and demand payment, usually in tough-to-trace cryptocurrencies, for their release. Often there’s a time window after which the attacker promises to destroy the digital assets.
With RaaS, attackers don’t just block access and demand ransom — double, triple, and even quadruple extortion became a norm. RaaS groups leak victims’ proprietary data and demand another ransom to stop. If victims refuse to pay, they launch DDoS attacks and begin harassing business partners and customers, or other tools in their hacker arsenal. Few organizations are capable of fighting attacks from so many fronts.
“The modern RaaS model allows cybercriminals to become specialists and focus on their areas of expertise,” says Zugec. “While this allows attackers to cause much more damage, it also leads to more standardized tooling and practices, giving businesses an opportunity to study threat actors’ strategies and build adequate defenses.”
For instance, look at Maze, a widely used ransomware family. Maze authors developed code that took advantage of Windows Management Instrumentation (WMI), the infrastructure for managing data and operations on Windows operating systems. It destroys existing and future Windows backups.
By understanding how a specific ransomware family can abuse an extremely common tool like WMI, companies can set up and deploy use policies that reduce risk of misuse. You can learn more about this from the
Business Threat Landscape Report.
It’s important to pair efforts defending against how ransomware family signature codes wreak havoc with security efforts that focus on egress — how the ransomware breaches your business’s networks. That’s where the affiliates typically play their role, running spam email campaigns, launching brute force attacks, and taking advantage of unpatched vulnerabilities.
It means undertaking necessary security best practices: multi-factor authentication (MFA), near-real-time patching of vulnerabilities, and continual security awareness training.
Cybercriminals are evolving, so should your defense
Like all security, calculating the return on investment in keeping ransomware at bay is about justifying that investment against what-if scenarios.
Ransomware attacks cost far more than the ransom that a business pays (if it chooses to pay it):
- There’s the downtime costs when no work is being done and no customers are being served.
- There’s the remediation costs to restore, rebuild and reinforce systems.
- There’s the increased insurance costs.
- Finally, there’s the hit to the business’s reputation that can linger long after all signs of an attack are gone.
“While RaaS attacks are more devastating, they also give more opportunities for defenders to detect and respond to an ongoing attack,” says Zugec. “Defense-in-depth and multilayered security is critical.” Learn how to proactively protect your business against ransomware.
If you are interested in learning more about protecting your small to medium sized business, read here.